Configuring IPsec IKEv2 Remote Access VPN Clients on macOS¶
It is possible to configure an IKEv2 type VPN manually in the macOS GUI without needing a VPN Profile configuration file. Basic configuration for IKEv2 is integrated into the network management settings the same as other connections, but it is quite limited.
Tip
The ipsec-profile-wizard package on pfSense Plus software generates a set of files which can automatically import VPN settings into Apple macOS and iOS (VPN > IPsec Export: Apple Profile) as well as Windows clients (VPN > IPsec Export: Windows).
This feature allows much greater flexibility in settings as it will configure clients to match what is set on the server specifically rather than making the server accommodate the default settings on various operating systems.
This package is exclusive to pfSense Plus software and is not available on the community edition.
If the package is not already installed, add it using the Package Manager.
Warning
The best practice is to use a VPN profile, such as from the Apple Configurator or IPsec Export Package. A profile requires less configuration on the client and can use options which are more secure and offer faster performance than the client attempts by default. Additionally, without using a profile it may not be possible to create a mobile IPsec configuration which can natively allow connections from different client types.
Import the CA Certificate into macOS¶
The VPN Server CA Certificate must be imported before a client can connect.
Copy the CA Certificate to the macOS system
Double-click the CA Certificate File in Finder (Figure macOS Certificate File in Finder), which opens Keychain Access
macOS Certificate File in Finder¶
Set Keychain to System on the Add Certificates dialog
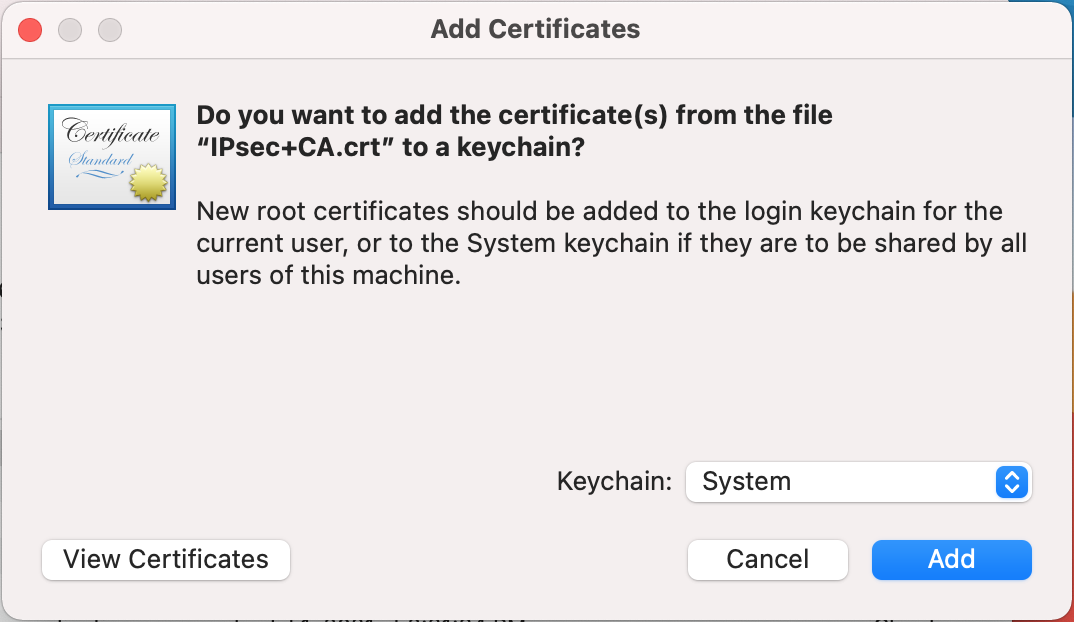
macOS Keychain Access Add Certificate¶
Click Add
Note
If this dialog does not appear and the CA is added into another keychain, locate it in Keychain Access and drag it into the System keychain.
Locate the imported certificate under System, Certificates as shown in Figure macOS Keychain Access System Certificate List
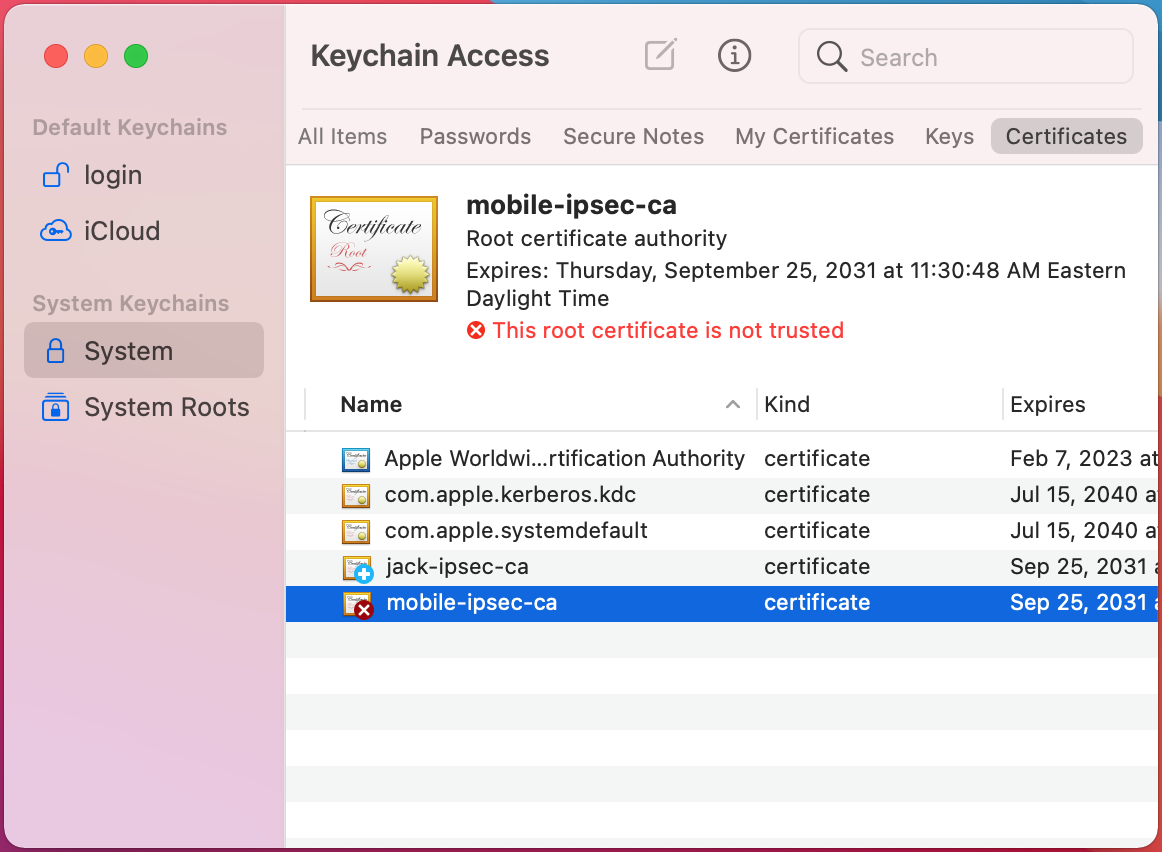
macOS Keychain Access System Certificate List¶
Click the Certificate
Click File > Get Info
Expand Trust
Set When using this certificate to Always Trust as shown in Figure macOS Certificate Trust Settings
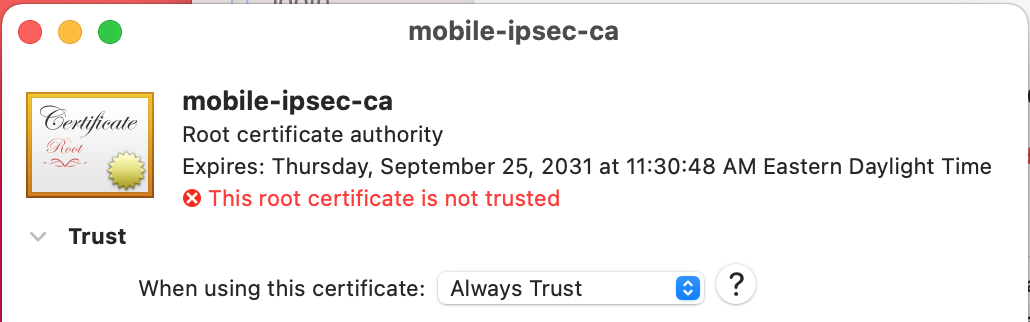
macOS Certificate Trust Settings¶
Click the red close button to close the certificate info window
This triggers an authentication prompt to allow the change.
Enter the login credentials and click Update Settings
Quit Keychain Access
The certificate is now located in System Certificates and has been marked as trusted so it can be used for the VPN.
Set up the VPN Connection¶
Open System Preferences
Click Network
Click the lock icon and enter credentials to make changes if the settings have not already been unlocked
Click + to add a new VPN entry as shown in Figure macOS Add Network Button
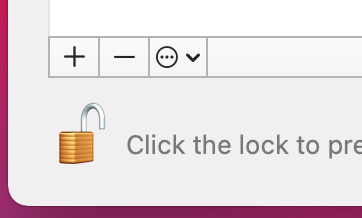
macOS Add Network Button¶
Select VPN for the Interface
Select IKEv2 for the VPN Type (default)
Set Service Name to a description for the VPN (e.g.
ExampleCo Mobile VPN) to complete the form, which will look similar to Figure macOS Create VPN Prompt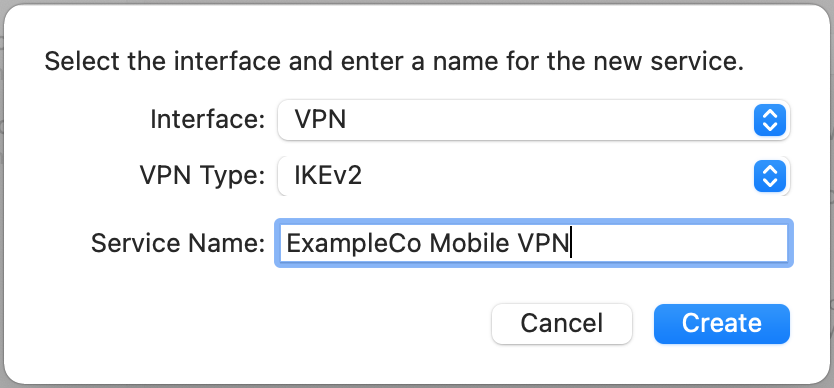
macOS Create VPN Prompt¶
Click Create
Enter the hostname of the firewall in DNS as the Server Address
Enter the hostname of the firewall again in Remote ID
Note
This must match the server certificate’s Common Name and SAN entry.
Leave Local ID blank, the settings will now look like Figure macOS IKEv2 VPN Settings
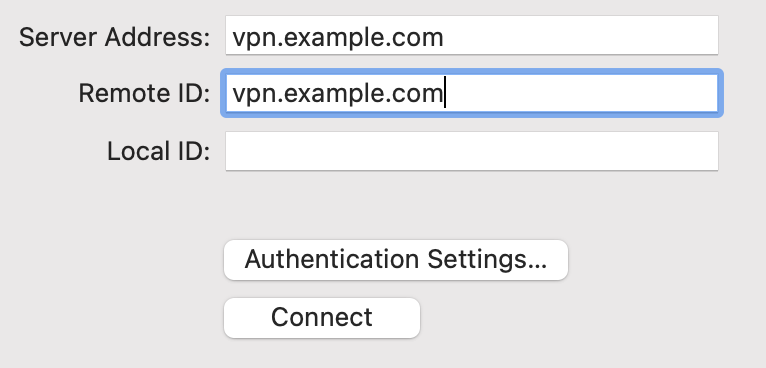
macOS IKEv2 VPN Settings¶
Click Authentication Settings
Select Username
Enter the Username and Password as shown in Figure macOS IKEv2 VPN Authentication Settings
Note
With EAP-MSCHAPv2 the Username is the Identifier configured for the user’s entry on the Pre-Shared Keys tab under VPN > IPsec. With EAP-RADIUS this would be the username set on the RADIUS server.
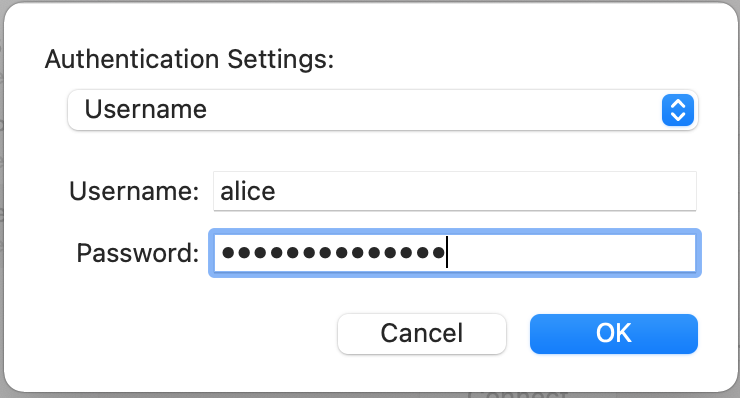
macOS IKEv2 VPN Authentication Settings¶
Check Show VPN status in the menu bar (if desired)
Click Apply
Connecting and Disconnecting¶
Managing the connection can be done multiple ways. The first method is to click Connect or Disconnect on the VPN entry in Network settings. The second, easier method is to check Show VPN Status in the menu bar in the VPN settings and then manage the connection from that icon, as shown in Figure macOS VPN Status Menu.
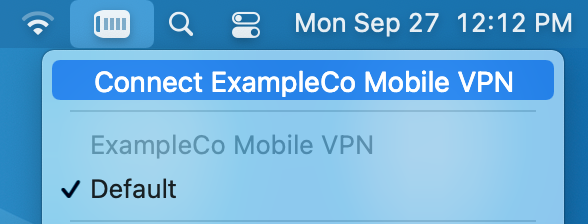
macOS VPN Status Menu¶