Configuring IPsec IKEv2 Remote Access VPN Clients on iOS¶
iOS version 9 and later have built-in capability for configuring a basic IKEv2 connection without a VPN Profile.
Tip
The ipsec-profile-wizard package on pfSense Plus software generates a set of files which can automatically import VPN settings into Apple macOS and iOS (VPN > IPsec Export: Apple Profile) as well as Windows clients (VPN > IPsec Export: Windows).
This feature allows much greater flexibility in settings as it will configure clients to match what is set on the server specifically rather than making the server accommodate the default settings on various operating systems.
This package is exclusive to pfSense Plus software and is not available on the community edition.
If the package is not already installed, add it using the Package Manager.
Warning
The best practice is to use a VPN profile, such as from the Apple Configurator or IPsec Export Package. A profile requires less configuration on the client and can use options which are more secure and offer faster performance than the client attempts by default. Additionally, without using a profile it may not be possible to create a mobile IPsec configuration which can natively allow connections from different client types.
Import the CA to the iOS Device¶
As with other clients, the CA certificate must be installed on the client. Importing the CA Certificate to the client device is a relatively easy process. The first step is to get the CA Certificate to the client device. The easiest way to accomplish this is via e-mail as shown in Figure iOS Mail Client Receiving CA Certificate
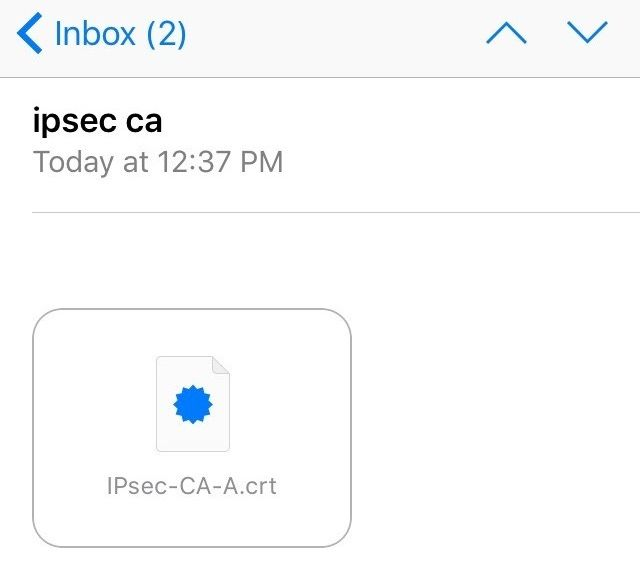
iOS Mail Client Receiving CA Certificate¶
To install the certificate from e-mail:
Send the CA Certificate only (not the key) to an e-mail address reachable from the client device
Open the Mail app on the client device
Open the message containing the CA Certificate
Tap the attachment to install the CA Certificate and a prompt labeled Install Profile will show as seen in iOS CA Certificate Install Profile Prompt
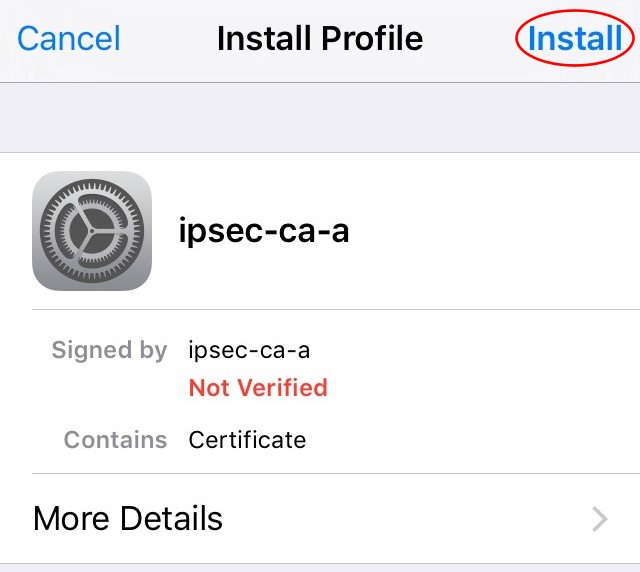
iOS CA Certificate Install Profile Prompt¶
Note
Newer versions of iOS may copy the CA to an entry under the Settings app for review before it can be installed. The device will instruct the user how to proceed when this happens. Typically, this involves opening the Settings app and tapping Profile Downloaded.
Tap Install in the upper right, and a warning screen is presented as shown in iOS CA Certificate Install Warning
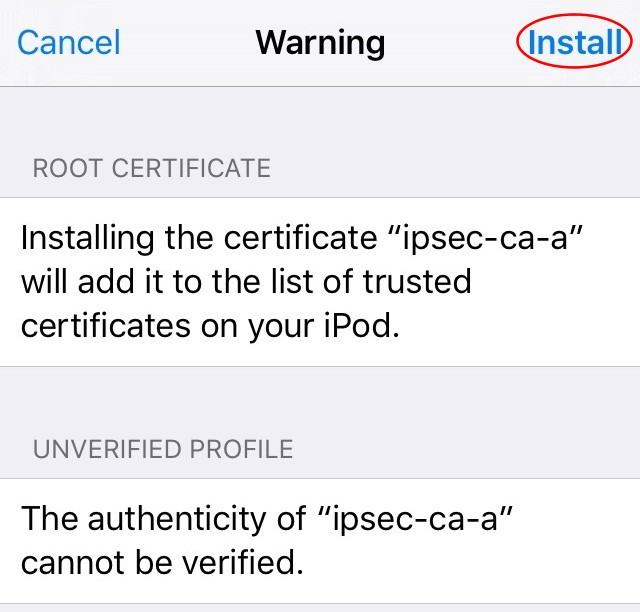
iOS CA Certificate Install Warning¶
Tap Install in the upper right once more to confirm and then one final prompt is presented as seen in iOS CA Certificate Confirmation Prompt
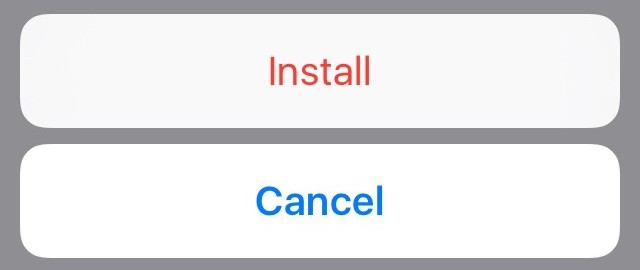
iOS CA Certificate Confirmation Prompt¶
Tap Install at the confirmation prompt and the CA Certificate is now stored as a trusted entry.
Set up the VPN Connection¶
Once the CA Certificate has been installed, a VPN entry must be configured:
Open Settings
Tap VPN
Tap Add VPN Configuration
Set Type to IKEv2 (default)
Fill in the settings as follows:
- Description:
A name for the VPN connection,
ExampleCo VPN- Server:
The hostname of the firewall in DNS
Note
This must match a SAN value in the server certificate.
- Remote ID:
The hostname of the firewall again
Note
This must match a SAN value in the server certificate.
- Local ID:
Leave blank
- User Authentication:
Username
- Username:
The username for this user.
Note
With EAP-MSCHAPv2 the Username is the Identifier configured for the user entry on the Pre-Shared Keys tab under VPN > IPsec. With EAP-RADIUS this would be the username set on the RADIUS server.
- Password:
The password for this user.
Tap Done to complete the VPN entry. When complete, it looks similar to iOS IKEv2 Client Settings
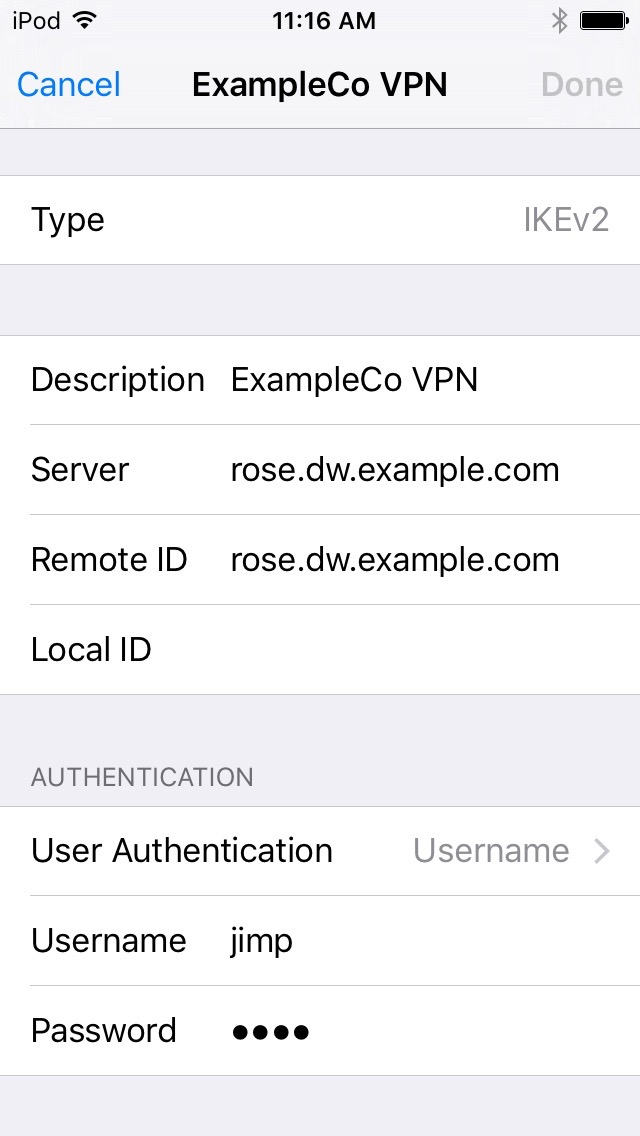
iOS IKEv2 Client Settings¶
Connecting and Disconnecting¶
The VPN may be connected or disconnected by visiting the VPN entries under Settings. This varies a bit but typically shows in at least two places:
Settings > VPN
Settings > General > VPN
The entry directly under Settings appears near the top of the list with the other Network entries (Airplane mode, Wi-Fi, and Bluetooth) once there is at least one VPN connection present.
Once in the VPN list, the VPN entry must be selected (shows a checkmark next to its entry) and then the slider may be moved to the “On” position to connect.
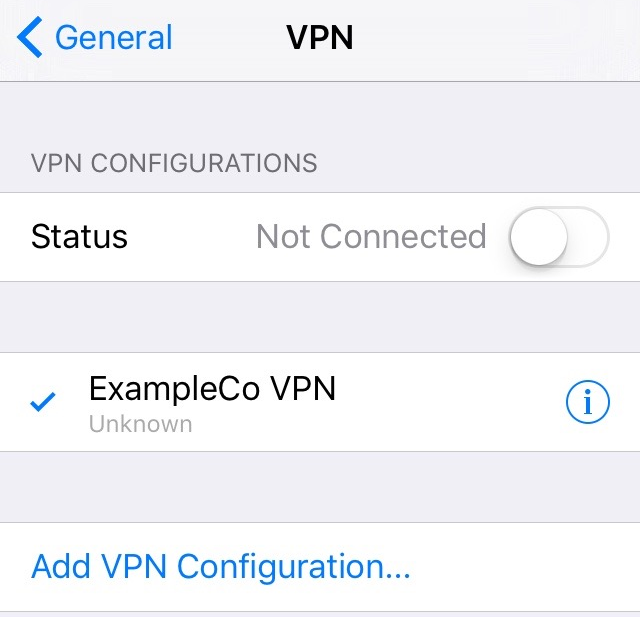
iOS VPN List¶