Preventing RFC 1918 Traffic from Exiting a WAN Interface¶
RFC 1918 addresses are blocks of network IP addresses reserved for private
use. These addresses are commonly used behind firewalls to allow a single public
IP address to be shared with multiple devices using NAT. The default pfSense®
software installation assigns the 192.168.1.0/24 address space to the LAN
interface, but RFC 1918 also defines other CIDR ranges for private use:
10.0.0.0/8172.16.0.0/12192.168.0.0/16
As a general rule, it is good practice to prevent network traffic intended for RFC 1918 subnets from leaving the firewall via the WAN interface. This avoids unnecessary traffic on the WAN link and also provides a small security benefit by keeping information about the LAN network behind the firewall.
An example where this rule can be helpful is if a machine on the local LAN (e.g.
192.168.1.5) is configured to access private LAN addresses that are routed
across a VPN tunnel (e.g. 192.168.100.0/24). If the VPN link were to go
down, the firewall would no longer have an active route for 192.168.100.0/24
and a packet intended for 192.168.100.0/24 will be routed out the WAN
interface using the default route. This could potentially provide information
about the private LAN to someone with access to the ISP network. A malicious
user could even set up an impostor machine on the WAN with a
192.168.100.0/24 address and pretend to be a machine on the inactive VPN
link.
While the chance of this being a problem is small, the probability of unintentional RFC 1918 traffic routing through the WAN interface will increase for installations with more complex LAN topologies, numerous users (typos, etc.), or routes that may frequently change (VPN, etc.). In these scenarios, it may be beneficial to add a firewall rule preventing RFC 1918 traffic from being routed out of the WAN interface.
Scenarios where RFC 1918 addresses should NOT be blocked on the WAN interface¶
The default configuration of pfSense software will not block RFC 1918 addresses routed from the LAN subnet to the outside WAN because there are two common scenarios where blocking this traffic is not desirable:
- ISP assigns an RFC 1918 address to end users:
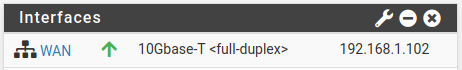
Some ISPs assign private network addresses to their customers and perform their own NAT for customer traffic to the public internet. Verify this by looking at the WAN interface IP address on the dashboard. If the assigned address is from one of the private IP ranges listed above, RFC 1918 traffic should NOT be blocked.
- The firewall is behind another firewall or router:
In this case, pfSense software performs NAT for devices connected to the LAN. The WAN interface forwards traffic to the upstream device where it undergoes a second NAT operation before entering the public internet. This is verified using the same steps as above – if the WAN IP address is from the RFC 1918 range, do NOT block this traffic from exiting the WAN
This is an example of an RFC 1918 address assigned to the WAN:
Warning
If either of these scenarios apply to this installation of pfSense software, do NOT add additional RFC 1918 traffic blocking to the WAN interface as this may prevent LAN users from accessing the WAN.
Steps to block RFC 1918 traffic from leaving the WAN interface¶
For installations where the above scenarios do not apply an additional firewall rule can be put in place to prevent RFC 1918 traffic from leaking out of the WAN interface. This provides a small increase in security and privacy by preventing information about the local LAN from being routed further upstream to the ISP.
To add a block rule for RFC 1918 traffic:
Navigate to Firewall > Aliases
Click
 Add to create a new alias
Add to create a new aliasConfigure the alias with these settings:
- Name:
private_networks(Or another relevant name such asRFC1918)- Description:
RFC 1918 Private Networks- Type:
Network(s)
- Network or FQDN:
Add entries for each of the private RFC 1918 subnets:
10.0.0.0/8172.16.0.0/12192.168.0.0/16
Click Save
Navigate to Firewall > Rules, Floating tab
Click
 to add a new rule to the top of the list
to add a new rule to the top of the listConfigure the rule with these settings:
- Action:
Reject
- Quick:
Checked
- Interface:
WAN
Optionally select multiple WAN interfaces or interface groups here, do NOT select the local LAN
- Direction:
out
- Address Family:
IPv4
- Protocol:
any
- Source:
any
- Destination:
Address or Alias,
private_networks
Click Save
Click Apply Changes
Lastly, verify that local LAN and internet connectivity are still functional.
Notes¶
Adding this rule to the firewall will block access to bridge devices like cable
modems or upstream routers outside the WAN interface. For example, many cable
modems use an IP address of 192.168.100.1 by default. This may or may not be
desirable behavior for users. The RFC 1918 firewall rule needs to be bypassed
with a specific pass rule above it, or disabled, if clients inside the LAN
require access to this type of device.
On the interface options (Interfaces > WAN, for example) there is an option to Block private networks. This is a rule blocking inbound traffic, not outbound like the rule described here. As long as the firewall is not behind a WAN that uses private addressing, both types of rules are desirable and should be enabled.