Granting Users Access to SSH¶
This recipe explains how to enable Secure Shell (SSH) access to the firewall.
SSH is typically used for debugging and troubleshooting, but has many other useful purposes.
Note
The SSH daemon is not required by the firewall for operation, so it is disabled by default.
See also
Enable SSH via GUI¶
This example enables SSH access using only public key authentication, which is more secure than allowing access by password alone.
Navigate to System > Advanced, Admin Access tab
Check Enable Secure Shell
Set SSHd Key Only to Public Key Only to allow only key-based SSH authentication
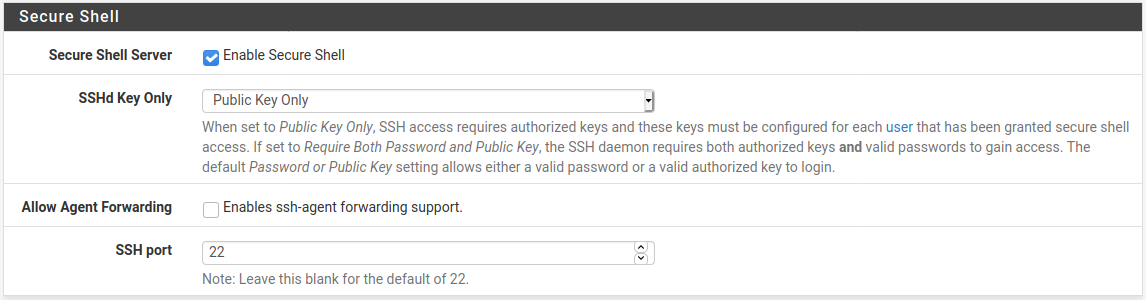
Enter a port number in SSH Port if the SSH daemon should listen on a non-default port
Leave the field blank for the daemon to use port
22Click Save
SSH Keys¶
When the SSH daemon is set for key-based authentication, it uses the keys
defined on user accounts. Add keys to individual user accounts under System >
User Manager. The admin user and root user share keys.
Warning
Do not attempt to manage keys from the shell directly.
See also
Enable SSH via Console¶
Connect to the console (VGA or Serial) and use option 14 to enable or
disable SSH.
To change the port number or key authentication options, use the GUI as directed above.
SSH Daemon Security¶
With a default ruleset, SSH may only be accessed by clients on the LAN. If SSH access must be allowed for clients the WAN, the best practice is to restrict access to Key-based authentication to avoid issues with brute force attacks. Moving the daemon to an alternate port is also a good practice, but moving the port alone is not sufficient protection.
The firewall will automatically block users who attempt to authenticate unsuccessfully. This behavior, and settings to control it, are described in Login Protection.
If password authentication is active, ensure that all user accounts with shell access have strong passwords that cannot be easily guessed.
See also
See Best Practices for SSH for more on SSH security.
User Access¶
By default, only admin and root have SSH access. Additional users with
limited access may be granted the User - System - Shell account access
privilege to login via SSH.
Note
Additional users do not have full root privileges in the shell, so the system does not display the console menu for those users. Many commands and other files are inaccessible as well. For a normal user to get much use from the shell, the Sudo Package can delegate additional privileges to run commands as root or other users.
SCP File Transfers¶
For information on using SCP file transfers via SSH, see Accessing Files on the Firewall with SCP.