WAN Connectivity with 802.1X Authentication Bridging and VLAN 0 PCP Tagging¶
Some Internet Service Providers require their customers to utilize the ISP modem in conjunction with an Optical Network Terminal (ONT) to be granted access to their fiber network. AT&T is one major example of such a provider. However, in some cases it is possible to bypass the modem and connect a firewall directly.
This guide covers the process of configuring a firewall to accommodate this type of authentication.
Note
This guide primarily applies to the AT&T Residential Fiber Network in North America, but can be adapted to any ISP utilizing a similar configuration.
Warning
The configuration options used in this guide are only present on pfSense® Plus software version 23.05-RELEASE and later.
Use Case¶
The purpose of this configuration is to provide authentication for access to the fiber network. Some ISP modems offer an “IP-Passthrough” mode which enables end users to have their public IPv4 and IPv6 addresses/blocks assigned directly to the equipment behind it (i.e. the firewall). However, this comes with a few drawbacks:
- Modem Memory Limitations
The fiber modem may still track states even in IP-Passthrough mode. Some modems have a hard limit on the number of states that they can handle at a time, becoming unstable under significant load.
- Limitations in IPv6 Implementation
In IP-Passthrough mode the modem is usually provisioned with an IPv6 prefix (
/60for AT&T, for example), but will only hand out a single/64prefix out of the larger allocation via DHCP-PD to the firewall. This means that only a single LAN on the firewall can be provisioned with IPv6 by default. It is possible to request multiple/64networks out of the IPv6 prefix block, but that is an ugly workaround.- Multiple Points of Failure
Having an ONT, a modem, and a firewall all needing to be powered at all times and available at all times introduces unnecessary additional points of potential hardware failure that can bring down connectivity even if the physical fiber link is in working order.
Bypassing the ISP equipment and attaching directly to the ONT with a pfSense Plus firewall eliminates or reduces the above limitations, allowing for greater control and flexibility.
Warning
The best practice when bypassing the ISP modem is to disable the Wi-Fi Access Point in the ISP equipment. This scenario requires an alternate means of Wi-Fi and switch connectivity behind the firewall to ensure connectivity parity with the ISP-provided all-in-one solution for Wi-Fi connectivity.
Requirements¶
Authenticating the firewall and allowing it to connect to the provider requires the following:
A firewall with at least three unique, discrete interfaces: One for the modem, one for the WAN/ONT connection, and one for the inside network(s).
The modem must be able to authenticate access using 802.1X EAP-TLS authentication. ISP modems using this type of 802.1X authentication have a “burned in” certificate and will initiate authentication when attached to a physical network on the red “ONT” port. This is handled on boot-up of the modem normally when it is in-line between the ONT and the local equipment, and it will periodically retry authentication.
All traffic after authentication must be 802.1Q tagged on VLAN
0with a Priority Code Point (PCP) of1. PCP is a means of defining traffic priority. A PCP of1is “Best Effort” and is how most ISPs, including AT&T, expect traffic to be marked. Configuring a PCP on a non-VLAN interface in pfSense Plus will tag the traffic on VLAN0and include the PCP value.The WAN interface on pfSense Plus software must have the MAC address spoofed to match the WAN interface of the fiber modem. This MAC address may be printed on sticker attached to the modem, or it may be visible in the web interface on the modem.
The pfSense Plus software interface attached to the modem must be set to operate in promiscuous mode.
The firewall must send all IPv6 DHCP requests with a defined and expected DUID. A DUID is a unique identifier a device uses when requesting a DHCPv6 lease. Normally pfSense software will use an automatically generated random identifier, but ISPs such as AT&T expect a DUID-EN (DUID Enterprise Number) of
3561and an identifier tied to the serial number of the modem. The identifier for a modem can be generated using an open source script.See also
To learn more about DUIDs, see DHCP6 DUID.
The firewall must send a prefix hint when requesting a DHCPv6 Prefix Delegation. Typically, this is
/60for AT&T. A/60prefix allows for 16 interfaces to each have a unique /64 subnet assigned from this block.
Modem Bypass Configuration¶
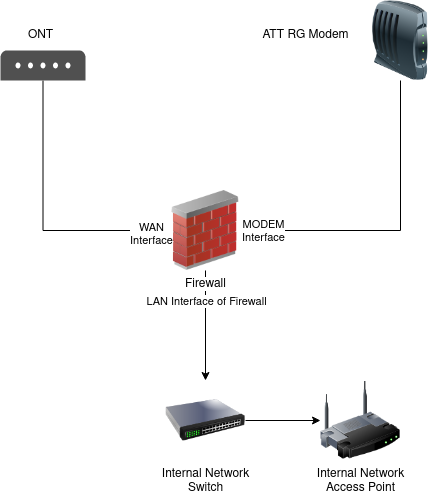
Diagram of Auth Bridge Wiring Layout¶
Physical Connections¶
Set up the physical connections as shown in Diagram of Auth Bridge Wiring Layout:
Connect the ONT device LAN/Modem port to the NIC on the firewall which will be the WAN interface
Connect the ISP modem ONT/WAN port (may be marked in red) to the NIC on the firewall which will be the MODEM interface
Connect the NIC on the firewall which will be the LAN interface to a switch or other means of local connectivity
Configure Firewall Interfaces¶
The next step is to configure the interfaces in the pfSense Plus software GUI.
Modem Interface¶
Assign and configure a new interface for the ISP Modem:
Navigate to Interfaces > Assignments
Set Available network ports to the physical interface attached to the ISP Modem
Click
 Add
AddNote the name of the new interface (e.g. OPT1)
Navigate to the newly added OPT interface using the Interfaces menu (e.g. Interfaces > OPT1)
Configure the interface options as follows:
- Enable interface
Checked
- Description
MODEM- IPv4 Configuration Type
None
- IPv6 Configuration Type
None
- Enable Promiscuous Mode
Checked
Click Save
Click Apply Changes
The interface will now be available at Interfaces > MODEM and will appear as a choice with that name in various interface fields in the GUI.
WAN/ONT Interface¶
Now configure the WAN interface to send traffic that the ONT and ISP will accept:
Navigate to the interface attached to the ONT (e.g. Interfaces > WAN)
Configure the options as follows:
- Enable interface
Checked
- Description
WANor another similarly descriptive name- IPv4 Configuration Type
DHCP
- IPv6 Configuration Type
DHCP6
- MAC Address
Enter the MAC address of the WAN interface on the ISP Modem
- Priority Tag
1- DHCPv6 Prefix Delegation size
Set to match the value provided by the ISP, e.g.
60for AT&T- Send IPv6 prefix hint
Checked
- Do not wait for a RA
Checked
Click Save
Click Apply Changes
LAN Interface¶
Finally, configure the LAN and other local interfaces:
Navigate to Interfaces > LAN or its equivalent
Configure the options as follows:
- Enable interface
Checked
- Description
LANor another similarly descriptive name- IPv4 Configuration Type
Static IPv4 using whichever private LAN subnet is already in place.
- IPv6 Configuration Type
Track Interface
- Track IPv6 Interface
- IPv6 Interface
WAN or whichever interface is attached to the ONT
- IPv6 Prefix ID
1
Click Save
Click Apply Changes
Repeat this for any remaining inside interfaces. For each additional interface,
increment the IPv6 Prefix ID value by 1 in hexadecimal. On AT&T or
other providers who delegate a /60 prefix size, the maximum ID value is
f. The help text under the IPv6 Prefix ID field is automatically
adjusted to show the minimum and maximum allowed values for the ID.
Configure IPv6 DUID¶
Set the custom DUID to send to the ISP:
Navigate to System > Advanced, Networking tab
Configure the options on the page as follows, leaving other unmentioned options at their current values:
- DHCP6 DUID
DUID-EN: Assigned by Vendor based on Enterprise Number
- DUID-EN
- IANA Private Enterprise Number
3561- Identifier
Enter the DUID value generated by the gen-duid.sh script
Click Save
Configure Authentication Passthrough¶
Passing through the authentication traffic between the modem and ISP requires two Ethernet rules to bridge the appropriate traffic.
Enable Ethernet Rules¶
The Ethernet rules feature is disabled by default and must be manually enabled before use:
Navigate to System > Advanced, Firewall & NAT tab
Check Enable Ethernet Filtering in the Advanced Options section
Click Save
See also
Add WAN-Modem Bridge Rule¶
Add a rule to bridge 802.1X authentication traffic from the WAN/ONT to the MODEM interface:
Navigate to Firewall > Rules, Ethernet tab
Click
 Add
AddConfigure the rule as follows:
- Action
Pass
- Quick
Checked
- Interface
WAN or whichever interface is attached to the ONT
- Direction
in
- Protocol
IEEE 802.1X
- Source
any
- Destination
any
Click Display Advanced and set:
- Bridge To
MODEM
Click Save
Add Modem-WAN Bridge Rule¶
Add a rule to bridge anything sent by the ISP Modem to the WAN interface:
Navigate to Firewall > Rules, Ethernet tab
Click
 Add
AddConfigure the rule as follows:
- Action
Pass
- Quick
Checked
- Interface
MODEM
- Direction
in
- Protocol
Any
- Source
any
- Destination
any
Click Display Advanced and set:
- Bridge To
WAN or whichever interface is attached to the ONT
Click Save
Click Apply Changes
Finish Up¶
The modem bypass configuration is now complete. Reboot the firewall to ensure the settings are applied completely. During the boot sequence, the modem should detect the link change and begin transmitting 802.1X authentication requests across the Layer 2 filter to the WAN interface, and the WAN interface should be able to acquire a DHCP and DHCPv6 lease.