Port Forwarding¶
Port forwarding is a type of inbound NAT which enables access to a specific port, port range, or protocol on an internal network device. Port forward rules rewrite the destination of a packet and then forward those packets to the new destination. This functionality is known by different names in various products, including “Destination NAT” or “Inbound NAT”.
To configure port forwarding rules, navigate to Firewall > NAT, on the Port Forward tab.
“Port Forward” is a term familiar to users, but it is an oversimplification. Port forward rules can redirect entire protocols such as GRE or ESP in addition to redirecting specific TCP, UDP, and SCTP ports.
The most common uses of port forward rules are for hosting servers or using applications which require inbound connections from the Internet.
See also
Hangouts Archive to view the May 2016 hangout for NAT on pfSense software version 2.3, The June 2016 hangout on Connectivity Troubleshooting, and the December 2013 Hangout on Port Forward Troubleshooting, among others.
Port Forwarding Risks¶
In a default configuration, pfSense® software does not allow any connections initiated from hosts on the Internet. This provides protection from attackers scanning the Internet searching for targets. Using port forward rules, and corresponding firewall rules allows connections matching the rules through to local targets, potentially exposing them to attackers. The firewall does not know the difference between a packet with a malicious payload and one that is benign. However, the exposure is limited to the parameters set inside the port forward and corresponding firewall rule. Even if the firewall rules were to allow any inbound packets, the internal host would still only be exposed on ports/protocols set in the port forward rules.
Target systems must use local host-based controls to secure services forwarded through the firewall.
Port Forwarding and Local Services¶
Port forwards take precedence over services running locally on the firewall, such as the web interface, VPNs, and SSH. For example, say an administrator intended to allow remote web interface access on the WAN from a remote office using HTTPS on TCP port 443. A port forwarding rule on WAN for TCP 443 will take precedence and the web interface will no longer be accessible from the remote office through the WAN. This does not affect access on other interfaces, only the interface on the overlapping port forward rule.
Port Forward Rule Precedence¶
For inbound packets, port forward rules take precedence over 1:1 NAT rules. This allows port forwards to override 1:1 NAT rule behavior and forward specific ports to different internal targets or even the firewall itself.
Port Forward Rule Options¶
When creating or editing a port forward rule, the following settings are available:
- Disable:
Toggles whether this rule is active.
- No RDR (NOT):
Prevents the firewall from redirecting packets matching the rule as they arrive. This is necessary if the packets would otherwise match a port forward rule, but those packets should not be redirected by the firewall.
This can override a forwarding action, which may be useful to allow access to a service on the firewall itself on an IP address used in 1:1 NAT rules, or another similar advanced scenario.
Most configurations will not use this field.
- Interface:
The ingress interface where this rule will apply.
Typically, this is WAN or a WAN-type interface, but in some special cases it could be LAN or another internal interface.
- Address Family:
The address family for which this port forward rule will apply, either IPv4 or IPv6.
This must match the address family of the destination IP address and redirect target IP address.
When an interface contains addresses of both families, the firewall will use the appropriate matching address. Additionally, when selecting an interface it must have an IP address which matches this family.
- Protocol:
The IP protocol this port forward rule will match.
This must be set to match the type of service the rule is forwarding, whether it is TCP, UDP, or another available choice.
Most common services are TCP or UDP, but consult the documentation for the service to confirm the correct value. The TCP/UDP option forwards both TCP and UDP together in a single rule.
Warning
Though it can be tempting to use the TCP/UDP choice when the exact value is unclear, the best practice is to only allow in the specific protocol the service requires. Otherwise, a different unapproved daemon could be run on the target host to receive connections for the other protocol.
The page will display controls for ports when the Protocol is set to TCP, UDP, TCP/UDP, or SCTP.
- Source:
The source network and port which this rule will match to limit redirection.
These options are hidden behind an Advanced button by default, and set to any source.
The Source options restrict which source IP addresses and ports can access this port forward rule. These restrictions are not typically necessary, but can offer increased security if remote sources are limited and static.
If the port forward must be reachable from any location on the Internet, the source must be any. For restricted access services, use an alias here so only a limited set of IP addresses may access the port forward.
Unless the service absolutely requires a specific source port, the Source Port Range must be left as any since nearly all clients will use randomized source ports.
Tip
If a role requires source restrictions, a better practice is to use a VPN to allow access to these services instead of port forwarding or firewall rules. However, that may not always be viable.
- Destination:
The destination address this rule will match.
This is the external IP address which is the original destination of an incoming packet which the rule will redirect.
For port forward rules on WAN, in most cases this is WAN Address. If multiple public IP addresses are available, the destination may be a Virtual IP on WAN.
Invert Match changes the behavior, so the port forward rule will match any packet that does not match the specified destination.
- Destination port range:
The destination port or range of ports this rule will match.
This is the external destination port which is the original destination port on an incoming packet which the rule will redirect.
Note
For a port forward rule to match a single port, enter the port in the From port box and leave the To port box blank.
The drop-down controls contain a list of common services. When set to Other, the fields can accept a port number or port alias name. When this field contains a port alias name, the same port alias name must be set as the Redirect target port.
- Redirect target IP:
The IP address where the rule will forward (redirect) incoming packets. The firewall will replace the original destination address on the packet with this address and then forward it to the new destination.
When using an IPv6 redirect target, it must be of the same scope as the destination. For example, it is not possible to forward between link-local scope addresses (
fe80::/10) and local (::1).Note
This field is only compatible with aliases that contain a single IP address.
An alias containing multiple addresses will cause the rule to redirect connections to target hosts in a round-robin fashion, but it is not ideally suited to that task. If one of the target hosts is down, the rule will still forward connections to the unreachable target.
For situations requiring forwarding to multiple hosts, such as load balancing or failover scenarios, use the HAProxy package.
- Redirect target port:
The port number where this rule will forward (redirect) incoming packets. The firewall will replace the original destination port on the packet with this port and then forward it to the new destination.
If the destination port is a range, this field defines where the forwarded port range begins. When a rule forwards a range of ports, e.g.
19000-19100, a rule can only define the local starting point since the number of ports in the range must be identical.This field allows a rule to redirect connections to a different port on the outside than the on the inside. For example, a port forward rule can redirect connections on external port
8888to local port80for HTTP on an internal server. A list of common services is available to pick from in the drop-down box.The drop-down controls contain a list of common services. When set to Other, the fields can accept a port number or port alias name. When this field contains a port alias name, the same port alias name must be set as the Destination port range.
- Description:
Text describing the rule, such as its intended behavior or name of a service. The best practice is to clearly describe the purpose of the rule in this field.
The description is optional and does not affect functionality of the rule.
- No XMLRPC Sync:
Prevents this rule from synchronizing to other High Availability cluster members via XMLRPC.
See also
Warning
This does not prevent a rule on a secondary node from being overwritten by the primary.
- NAT Reflection:
Overrides global NAT reflection behavior for this rule.
- Use system default:
Respects the global NAT reflection settings.
- Enable (NAT+Proxy):
Always performs NAT reflection for this rule using the NAT+Proxy method.
- Enable (Pure NAT):
Always performs NAT reflection for this rule using the pure NAT method.
- Disable:
Never performs NAT reflection for this rule.
- Filter Rule Association:
Optionally create a firewall rule which passes connections which matches the same packet parameters as this port forward rule.
Warning
This is very important. A port forwarding rule only defines which packets the firewall will redirect, a firewall rule allows those packets to pass through to the redirect target. Without a firewall rule to pass the packets, the firewall will drop them and there is nothing for it to forward.
The available choices are:
- None:
Does not create a firewall rule.
- Add associated filter rule:
Creates a firewall rule linked with this port forward rule.
If an administrator changes the port forward rule, the firewall automatically updates the firewall rule to match.
The firewall replaces this choice with an entry pointing to the new associated firewall rule on save.
This is the default behavior and the best choice for most use cases.
- Add unassociated filter rule:
Creates a firewall rule separate from this port forward rule.
If an administrator changes the port forward rule, they must also manually update the firewall rule to match.
This can be useful if the firewall requires options or restrictions that cannot be set on a port forward rule.
- Pass:
Uses a special PF keyword on the port forward rule that passes matching packets without the need of a firewall rule.
Because there is no firewall rule, the firewall forwards all packets matching this rule to the target host.
Note
Rules using Pass can only work on the interface containing the default gateway for the firewall, they do not work with Multi-WAN.
Configuring Port Forward Rules¶
Port forward rules are located at Firewall > NAT, on the Port Forward tab.
See also
The list of port forward rules works the same as the list of firewall rules for management. See Introduction to the Firewall Rules screen for details.
To create a new port forward rule:
Navigate to Firewall > NAT, Port Forward tab
Click
 Add to create a new port forward rule at the top of the
list
Add to create a new port forward rule at the top of the
listConfigure the rule as described in Port Forward Rule Options
Click Save
Click Apply Changes
Tracking Changes to Port Forward Rules¶
The firewall tracks changes to port forward rules in the same manner as firewall rules.
See also
Firewall rules automatically created by associated NAT rules are also marked as such in the tracking information on the associated firewall.
Port Forwarding Configuration Examples¶
This section contains example scenarios and configurations for port forwarding.
See also
Example Port Forward Rule for HTTP (TCP/80)¶
This example demonstrates how to configure a port forward rule to redirect HTTP
(TCP port 80) inbound on WAN destined to the WAN IP address to the internal
host at 10.3.0.15.
To configure this rule:
Navigate to Firewall > NAT, Port Forward tab
Click
 Add to create a new port forward rule at the top of the
list
Add to create a new port forward rule at the top of the
listConfigure the rule as described in Port Forward Rule Options with the following options:
- Interface:
WAN
- Address Family:
IPv4
- Protocol:
TCP
- Destination:
WAN Address
- Destination Port Range:
HTTP
- Redirect Target IP:
Address or Alias,
10.3.0.15- Redirect Target Port:
HTTP
- Description:
HTTP to web server
Click Save
Click Apply Changes
Figure Port Forward Example shows the port forward configuration page with these values:
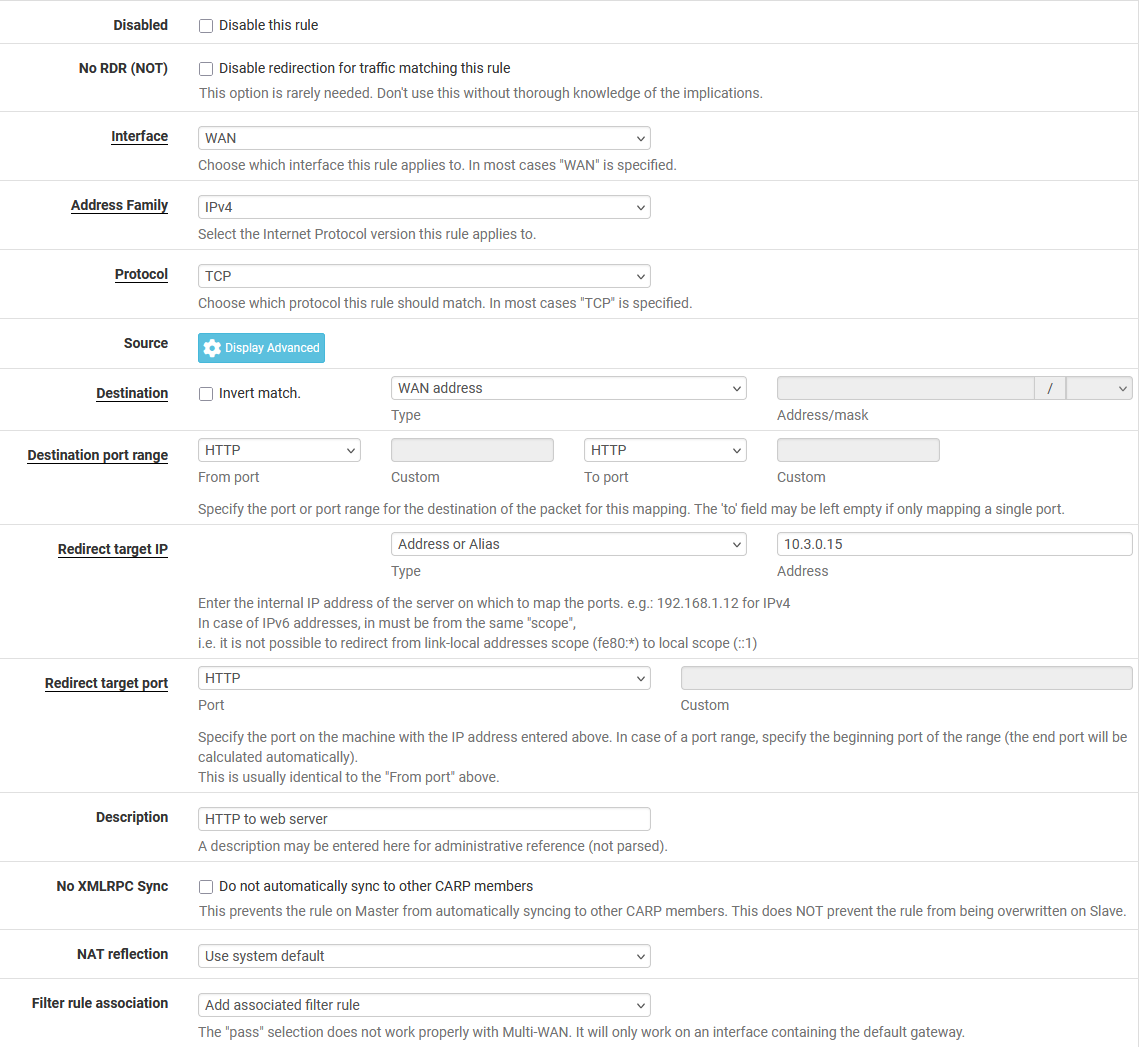
Port Forward Example¶
After clicking Save, the GUI displays the port forward rule list with the new rule, as shown in Figure Port Forward List.
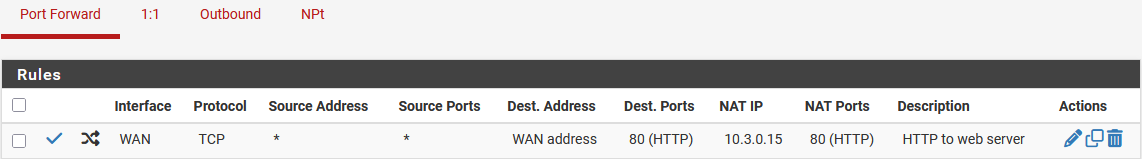
Port Forward List¶
Double-check the firewall rule at Firewall > Rules on the tab matching the port forward rule interface. The rule should show that it will pass connections in to the target IP address on the expected target port, as shown in Figure Port Forward Firewall Rule.

Port Forward Firewall Rule¶
If everything is configured correctly, the port forward rule will work when tested from outside the network.
See also
Accessing an Internal Target Using the External Destination Address¶
It takes additional work for clients behind the firewall to access services redirected by port forward rules using the external address. For example, when internal users must access public redirected services using hostnames from DNS.
This can be accomplished either by using NAT reflection or Split DNS, depending on the needs and capabilities of the clients.
Outbound Redirection with Port Forwards¶
Port forward rules can transparently redirect packets attempting to egress from an internal network. Port forward rules which specify the LAN interface or another internal interface will redirect packets matching the rule to the specified target. This is most commonly used for redirecting all outbound DNS to one server.
See also
Forwarding a Single Port to Multiple Targets¶
The firewall can only forward a single port to one internal host for each available public IP address when it forwards packets from any source.
For example, if a firewall has only one public IP address available, it can only
forward TCP port 80 to one internal web server. Any additional servers must
use alternate ports such as 8080.
If a firewall has five public IP addresses available as Virtual IP addresses,
then it can forward TCP port 80 to five internal web servers.
See also
Tip
For services such as HTTP and HTTPS, port sharing may be possible by using the HAProxy package. If the requests differ in some way, such as by different request hostnames, a proxy can make more advanced decisions about how to forward requests to multiple internal hosts.
The exception to this behavior is when port forward rules can match based on the source IP address of incoming connections.
If all sources are known in advance, rules can forward connections from those specific remote networks to different internal servers by matching those sources.
Figure Port Forward Example with Different Sources.
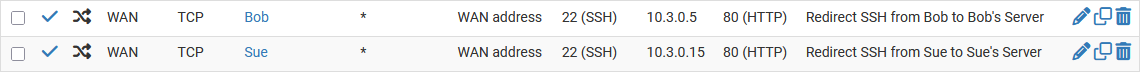
Port Forward Example with Different Sources¶
If only some sources are known in advance, rules can forward connections from specific remote networks to one server while a later rule can forward connections from any source on the same port to a different target.
Service Self-Configuration With UPnP IGD & PCP¶
Some programs support Universal Plug-and-Play (UPnP IGD) or Port Control Protocol (PCP) to automatically configure port forward rules and firewall rules. That approach has even more security concerns, but in home use the benefits often outweigh the potential drawbacks.
See also