UPnP IGD & PCP¶
Universal Plug and Play Internet Gateway Device (UPnP IGD) and Port Control Protocol (PCP) are network protocols which allow local software and devices to configure each other when attaching to a network. This includes autonomously creating dynamic NAT rules to redirect and pass incoming connections from remote hosts.
Note
PCP is the successor to NAT Port Mapping Protocol (NAT-PMP) and is compatible with clients using NAT-PMP.
The UPnP IGD & PCP service, located at Services > UPnP IGD & PCP, enables client devices such as computers and game consoles to autonomously allow required inbound traffic and can account for outbound NAT on traffic using the same ports. There are many popular programs and platforms which support UPnP IGD & PCP, such as Steam/Steam Deck, Nintendo consoles, PlayStation consoles, Xbox consoles, video conferencing apps, torrent clients, and more. PCP is supported primarily by Apple products but can also be found in other applications and devices.
See also
For advice on specific consoles and games, see Configuring pfSense Software for Online Gaming.
UPnP IGD & PCP Service Ports¶
The UPnP IGD daemon used by pfSense® software, miniupnpd, uses several ports
to communicate with clients. UPnP IGD employs the Simple Service Discovery
Protocol (SSDP) for network discovery, which uses UDP port 1900. PCP uses
UDP port 5351. The daemon also uses TCP port 2189 for HTTP and SOAP
queries.
Protocol |
Port |
Service |
|---|---|---|
UDP |
1900 |
SSDP |
TCP |
2189 |
HTTP/SOAP |
UDP |
5351 |
PCP |
When using a strict LAN firewall ruleset, manually add rules to allow access to these services, especially if the default LAN-to-any rule has been removed, or in bridge configurations.
UPnP IGD & PCP with IPv6¶
As of this writing, the UPnP IGD & PCP service on current versions of pfSense software is compatible with IPv6, but IPv6-capable client implementations are still rare.
Note
IPv6 UPnP IGD & PCP client traffic will almost always require manual rules to pass. Clients are likely to use a link-local source going to a multicast destination, which is not covered by the default interface rules.
Security Concerns¶
UPnP IGD & PCP are a classic example of the “Security vs. Convenience” trade-off. By their very nature, these services are insecure. Any program on the network can allow in and forward any traffic – a potential security nightmare. On the other side, it can be a chore to enter and maintain NAT port forwards and their associated rules, especially when it comes to game consoles. There is a lot of guesswork and research involved to find the proper ports and settings, but UPnP IGD & PCP just works and requires little administrative effort. Manual port forwards to accommodate these scenarios tend to be overly permissive, potentially exposing services that should not be open from the Internet. Manual port forwards are also always enabled, where UPnP IGD & PCP rules may be temporary.
Access controls in the UPnP IGD & PCP service configuration can lock down which devices are allowed to make port mappings and for which ports. Over and above the built-in access controls, further control may be exerted with firewall rules. When properly controlled, UPnP IGD & PCP can also be a little more secure by allowing programs to pick and listen on random ports, instead of always having the same port open and forwarded.
Configuration Options¶
Service Settings¶
- Enable port mapping service:
Master control for the entire UPnP IGD & PCP daemon. Also requires enabling one or both of the UPnP IGD or PCP/NAT-PMP protocols.
When unchecked, all the services on this page are disabled.
- Allow UPnP IGD Port Mapping:
When checked, clients can make requests using Universal Plug and Play Internet Gateway Device (UPnP IGD).
- Allow PCP/NAT-PMP Port Mapping:
When checked, clients can make requests using Port Control Protocol (PCP) and client requests using PCP-compatible protocols, such as the older NAT-PMP standard.
- External Interface:
The interface for outgoing traffic. This must be set to the single WAN containing the default gateway.
- Internal Interfaces:
The local interfaces where clients allowed to use UPnP IGD & PCP reside. Multiple interfaces may be selected.
Note
When using a bridge configuration, only select the bridge interface with an IP address.
External Address Settings¶
Port mapping with the UPnP IGD & PCP service requires a routable public IP address capable of receiving incoming connections from remote hosts. If this device is behind NAT, port forwarding may still be possible, provided the upstream router can forward traffic using an additional layer of NAT.
As the public address is key to its operation, the UPnP IGD & PCP port mapping service must be able to locate its routable public IP address, or it will refuse to allow port mapping.
If the External Interface has a public IP address, the settings in this section may be left empty or disabled (default) since the service can recognize that the interface address is public. If the interface has a private address, the service will refuse to map any ports without additional configuration.
If the External Interface is behind unrestricted NAT (e.g. 1:1 NAT), and the upstream router forwards incoming traffic to this device without any filtering, this service can still function so long as it can locate the correct public IP address.
The service can learn the public IP address and NAT type using an external server via the STUN protocol or if the address is static it can be hard-coded using the Override WAN Address setting.
- Enable STUN:
Enables retrieving the external IP address from a remote STUN server. When checked, the service will query an external STUN server to locate the routable public IP address for the external interface. This also tests inbound NAT connectivity to ensure forwarded traffic is delivered to this device.
This is useful for devices behind 1:1 NAT with a dynamic public address.
Warning
The service will disable port mapping if NAT testing determines inbound connections are not being forwarded to this device.
- STUN Server:
The hostname or IP address of a remote STUN server.
There are public STUN servers available, including:
stun.3cx.comstun.counterpath.com
- STUN Port:
The UDP port on which the STUN server is listening for client connections. The default port number is
3478.- Override WAN Address:
This option manually configures a public routable IP address this device can use to accept inbound connections.
This address can be an upstream static routable IP address with traffic forwarded to this device via NAT, or it can be an alternate routable IP address on this device, such as a virtual IP address.
Advanced Settings¶
- Download Speed:
Value to report when clients query the maximum link download speed, specified in kbit/s.
The default value is the link speed of the interface.
- Upload Speed:
Value to report when clients query the maximum link upload speed, specified in kbit/s.
The default value is the link speed of the interface.
- Traffic Shaping:
The name of an ALTQ (not Limiter) traffic shaping queue in which the firewall will place traffic passed by rules created via UPnP IGD & PCP.
Note
Exercise caution when selecting this queue. UPnP IGD & PCP can be used by traffic such as game consoles, which need high priority, and also by file transfer clients which may need low priority.
- Custom Presentation URL:
A custom URL this daemon presents to UPnP IGD & PCP clients who click this device when listing devices on the local network. For example, when browsing the network in Windows Explorer.
When left blank, the daemon uses the URL of the GUI on this device.
- Custom Model Number:
A custom model number presented to clients who click this device when listing devices on the local network. For example, when browsing the network in Windows Explorer.
When left blank, the daemon uses the current firmware version of this device.
- Firewall Logs:
When checked, rule generated by UPnP IGD & PCP will be set to log, so each connection matching these rules will appear in the firewall logs.
Note
The firewall logs can be viewed at Status > System Logs, on the Firewall tab.
- Uptime:
By default, the UPnP IGD & PCP daemon reports the service uptime when queried rather than the system uptime. Checking this option will cause it to report the system uptime (since last boot) instead.
Service Access Control Lists¶
- Default Deny:
When checked, UPnP IGD & PCP only allows access to client requests matching configured access control lists. This is a more secure method of controlling the service, but as discussed above, is also less convenient.
- ACL Entries:
ACL entries grant or deny access to the port mapping service based on several criteria.
Warning
These entries only control access for IPv4 clients, they do not apply to IPv6 clients.
Rules are formulated using the following format:
<[allow|deny]> <[external port|range]> <[internal IP|IP/CIDR]> <[internal port|range]>Click
 Add to create additional rules.
Add to create additional rules.Note
If the Default Deny option is enabled, rules must be set to allow access.
UPnP IGD & PCP User Permission Examples¶
Deny access to external port 80 forwarding from everything on the LAN,
192.168.1.0, with a /24 subnet, to local port 80:
deny 80 192.168.1.0/24 80
Allow 192.168.1.10 to forward any unprivileged port:
allow 1024-65535 192.168.1.10 1024-65535
Configuration Procedure¶
To configure UPnP IGD & PCP:
Navigate to Services > UPnP IGD & PCP
Configure the options as needed
Click Save
The UPnP IGD & PCP service will be started automatically.
UPnP IGD & PCP Status¶
To view a list of currently forwarded ports and clients, navigate to Status > UPnP IGD & PCP. The output will be similar to UPnP IGD & PCP Status Screen Showing Client PCs With Forwarded Ports.
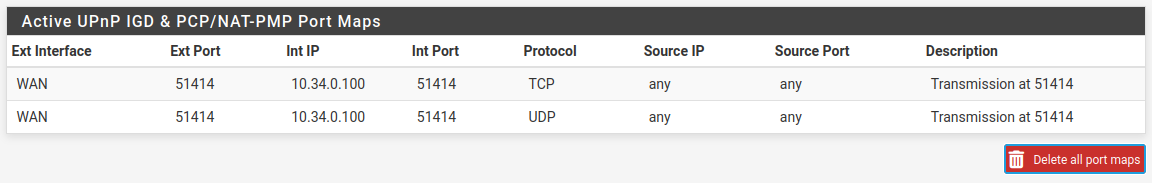
UPnP IGD & PCP Status Screen Showing Client PCs With Forwarded Ports¶
View the status of the UPnP IGD & PCP daemon at Status > Services. The Service Status page shows if the daemon is running or stopped, and allows the service to be stopped, started or restarted. Under normal circumstances, manually managing the daemon is not necessary.
Troubleshooting¶
Most issues with UPnP IGD & PCP tend to involve clients not being able to
communicate with the service. It is important to have firewall rules allow UPnP
IGD traffic on UDP port 1900. Since UPnP IGD uses multicast traffic, the
destination will be the broadcast address for the subnet, or in some cases a
destination of any will be necessary.
Note
For IPv6, it’s important to note that the traffic will almost always require manual rules to pass the traffic. Clients are likely to use a link-local source going to a multicast destination. That source is not covered by the default interface rules.
Consult the firewall logs at Status > System Logs, on the Firewall tab to see if traffic is being blocked. Pay particular attention to the destination address, as it may be different from expected.
Further trouble with game consoles may also be alleviated by switching to manual outbound NAT and enabling Static Port. See Static Port for more details.
If the WAN does not have a public address, or if the STUN NAT test fails, the
service can fail to add NAT mappings when clients make requests. The routing log
will contain messages such as Failed to add. The routing log also contains
other messages from the daemon at startup indicating these test results.
See also
For advice on specific consoles and games, see Configuring pfSense Software for Online Gaming.