Ordering of NAT and Firewall Processing¶
Understanding the order in which PF performs firewall and NAT actions is important when configuring NAT and firewall rules. Figure Ordering of NAT and Firewall Processing illustrates the basic logical order. The figure also depicts where tcpdump ties in, since its use as a troubleshooting tool is described later in this documentation in Packet Capturing.
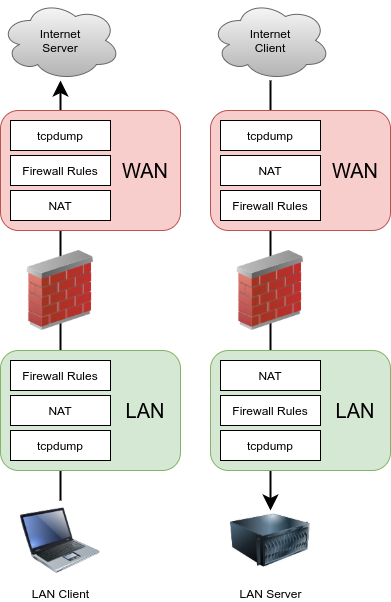
Ordering of NAT and Firewall Processing¶
Each layer is not always hit in typical configurations, but the use of floating rules or manual outbound NAT or other more complicated configurations can hit each layer in both directions. The diagram only covers basic scenarios for inbound and outbound traffic.
In terms of how the ruleset is processed, the order is:
Ethernet rules
Outbound NAT rules
Inbound NAT rules such as Port Forwards (including
rdr passand UPnP IGD & PCP)Rules dynamically received from RADIUS for IPsec and OpenVPN clients
Internal automatic rules (pass and block for various items like lockout, snort, DHCP, etc.)
User-defined rules:
Rules defined on the floating tab
Rules defined on interface group tabs (Including IPsec and OpenVPN)
Rules defined on interface tabs (WAN, LAN, OPTx, etc.)
Automatic VPN rules
Firewall/NAT Processing Order Example¶
Traffic from LAN to WAN is processed as described in the following more detailed example. If a type of rules do not exist or do not match, they are skipped.
Ethernet rules inbound on LAN
Port forward rules then 1:1 NAT rules on the LAN interface (e.g. proxy or DNS redirects)
Firewall rules for the LAN interface:
Floating rules inbound on LAN
Rules for interface groups including the LAN interface
LAN tab rules
Note
This includes NAT64 rules, at which point the source and destination of matching IPv6 packets are translated to IPv4 as determined by the NAT64 rule parameters.
1:1 NAT rules then Outbound NAT rules on WAN
Floating rules that match outbound on WAN
Ethernet rules outbound on WAN
In this case, port forwards on WAN and WAN tab firewall rules do not apply.
For traffic initiated on the WAN, the order is the same, but direction is reversed:
Ethernet rules inbound on WAN
Port forward rules then 1:1 NAT rules on the WAN interface (e.g. public services)
Firewall rules for the WAN interface:
Floating rules inbound on WAN
Rules for interface groups including the WAN interface
WAN tab rules
1:1 NAT rules then Outbound NAT rules on LAN
Floating rules that match outbound on LAN
Ethernet rules outbound on LAN
tcpdump is always the first and last thing to see traffic, depending on the
direction. First, on the incoming interface before any NAT and firewall
processing, and last on the outbound interface. It shows what is on the wire.
(See Packet Capturing)
See also
See Rule Processing Order for more information about the firewall rule processing order.
Ethernet Rules notes¶
Ethernet (L2) rules are processed before NAT and traditional firewall rules (Floating, group, or per-interface) in the inbound direction. For outbound traffic, Ethernet rules are processed last after all other rules.
See also
Floating Rules notes¶
Floating rules without quick set process as “last match wins” instead of
“first match wins”. Therefore, if a floating rule is set without quick and a
packet matches that rule, then it also matches a later rule, the later rule will
be used. This is the opposite of the other tab rules (groups, interfaces) and
rules with quick set which stop processing as soon as a match is made. See
Floating Rules for more details on how floating rules operate.
Extrapolating to additional interfaces¶
The previous diagram and lists only illustrate a basic two interface LAN and WAN deployment. When working with additional interfaces, the same rules apply. Traffic between two internal interfaces behaves the same as LAN to WAN traffic, though the default NAT rules will not translate traffic between internal interfaces so the NAT layer does not do anything in those cases. If Outbound NAT rules exist that match traffic between internal interfaces, it will apply as shown.
Rules for NAT¶
On the way into an interface, NAT applies before firewall rules, so if the destination is translated on the way in (e.g. port forwards rules then 1:1 NAT on WAN), then the firewall rules must match the translated destination. In the typical case of a port forward on WAN, this means the rule must match a destination of the target private IP address on LAN.
For example, with a port forward for TCP port 80 on WAN with an automatically added firewall rule, Figure Firewall Rule for Port Forward to LAN Host shows the resulting firewall rule on WAN. The internal IP address on the port forward is 10.3.0.15. Whether using port forward rules or 1:1 NAT rules, firewall rules on all WAN interfaces must use the internal IP address as the destination.

Firewall Rule for Port Forward to LAN Host¶
On the way out of an interface, outbound NAT applies before firewall rules, so any floating rules matching outbound on an interface must match the source after it has been translated by 1:1 NAT rules or outbound NAT rules.