NAT Reflection¶
NAT reflection refers to the ability to access external services from the internal network using the external (usually public) IP address, the same as if the client were on the Internet. While many commercial and open source firewalls do not implement this functionality, pfSense® software has solid NAT reflection functionality, though some environments require a split DNS infrastructure to fully accommodate this feature.
Split DNS is the best practice to allow local clients to access local resources so that the firewall is not involved in “hairpin” routing of internal services between local hosts.
See also
Split DNS is covered at the end of this section in Split DNS.
Configuring NAT Reflection¶
To enable NAT Reflection globally:
Navigate to System > Advanced on the Firewall & NAT
Locate the Network Address Translation section of the page
Configure the NAT Reflection options as follows:
- NAT Reflection mode for Port Forwards:
There are three available choices for NAT Reflection mode for port forwards, they are:
- Disable:
NAT Reflection will not be performed, but it may be enabled on a per-rule basis.
- NAT + Proxy:
Enables NAT Reflection using a helper program to send packets to the target of the port forward. This is useful in setups where the interface and/or gateway IP address used for communication with the target cannot be accurately determined at the time the rules are loaded. Reflection rules for use with the proxy are not created for ranges larger than 500 ports and will not be used for more than 1000 ports total between all port forwards. This mode does not work with UDP, only with TCP. Because this is a proxy, the source address of the traffic, as seen by the server, is the firewall IP address closest to the server.
- Pure NAT:
Enables NAT Reflection using only NAT rules in PF to direct packets to the target of the port forward. It has better scalability, but it must be possible to accurately determine the interface and gateway IP address used for communication with the target at the time the rules are loaded. There are no inherent limits to the number of ports other than the limits of the protocols. All protocols available for port forwards are compatible. If servers are on the same subnet as clients, the Enable automatic outbound NAT for Reflection option will mask the source of the traffic so it flows properly back through the firewall.
- Reflection Timeout:
This option is only relevant to NAT + Proxy mode, and controls how long the NAT proxy daemon will wait before closing a connection. Specify the value in seconds.
- Enable NAT Reflection for 1:1 NAT:
This option allows clients on internal networks to reach locally hosted services by connecting to the external IP address of a 1:1 NAT entry. To fully activate the feature, check both Enable NAT Reflection for 1:1 NAT and Enable automatic outbound NAT for Reflection. The latter option is only necessary if clients and servers are in the same subnet.
- Enable automatic outbound NAT for Reflection:
When enabled, this option activates additional NAT rules for 1:1 NAT Reflection and Pure NAT mode NAT Reflection for port forwards. These additional rules mask the source address of the client to ensure reply traffic flows back through the firewall. Without this, connections between the client and server will fail as the server will reply directly back to the client using its internal IP address. The client will drop the connection since it expects a reply from the public IP address.
Click Save to activate the new NAT reflection options
NAT Reflection Caveats¶
NAT reflection is a hack as it loops traffic through the firewall when it is not necessary. Because of the limited options PF allows for accommodating these scenarios, there are some limitations in the pfSense NAT + Proxy reflection implementation. Port ranges larger than 500 ports do not have NAT reflection enabled in NAT + Proxy mode, and that mode is also effectively limited to only working with TCP. The other modes require additional NAT to happen if the clients and servers are connected to the same interface of the firewall. This extra NAT hides the source address of the client, making the traffic appear to originate from the firewall instead, so that the connection can be properly established.
Split DNS is the best means of accommodating large port ranges and 1:1 NAT. Maintaining a split DNS infrastructure is required by many commercial firewalls even, and typically isn’t a problem.
Split DNS¶
The best practice alternative to NAT reflection is deploying a split DNS infrastructure. Split DNS refers to a DNS configuration where, for a given hostname, public Internet DNS resolves to public IP address, and DNS on the internal network resolves to the internal, private IP address. The exact methods to accommodate split DNS vary depending on the specifics of the DNS infrastructure in an organization, but the end result is the same: NAT reflection is not necessary because hostnames resolve to the private IP addresses inside the network and clients contact the servers directly.
Split DNS allows servers to see the true client IP address, and connections between servers and clients in the same subnet go directly, rather than unnecessarily involving the firewall.
The only case that does not work properly with split DNS is when the external and internal port numbers are different. With split DNS, the port number has to be the same in both places.
DNS Resolver/Forwarder Overrides¶
If pfSense software is acting as the DNS server for internal hosts, then host overrides in the DNS Resolver or DNS Forwarder can provide split DNS functionality.
To add an override to the DNS Resolver:
Navigate to Services > DNS Resolver
Click
 the under Host Overrides to reach the Host Override
Options page
the under Host Overrides to reach the Host Override
Options pageConfigure the host override as needed, using the internal IP address of the server. See Host Overrides. Figure DNS Resolver Override for example.com shows an example of a DNS override for
example.comandwww.example.com.Click Save
Click Apply Changes
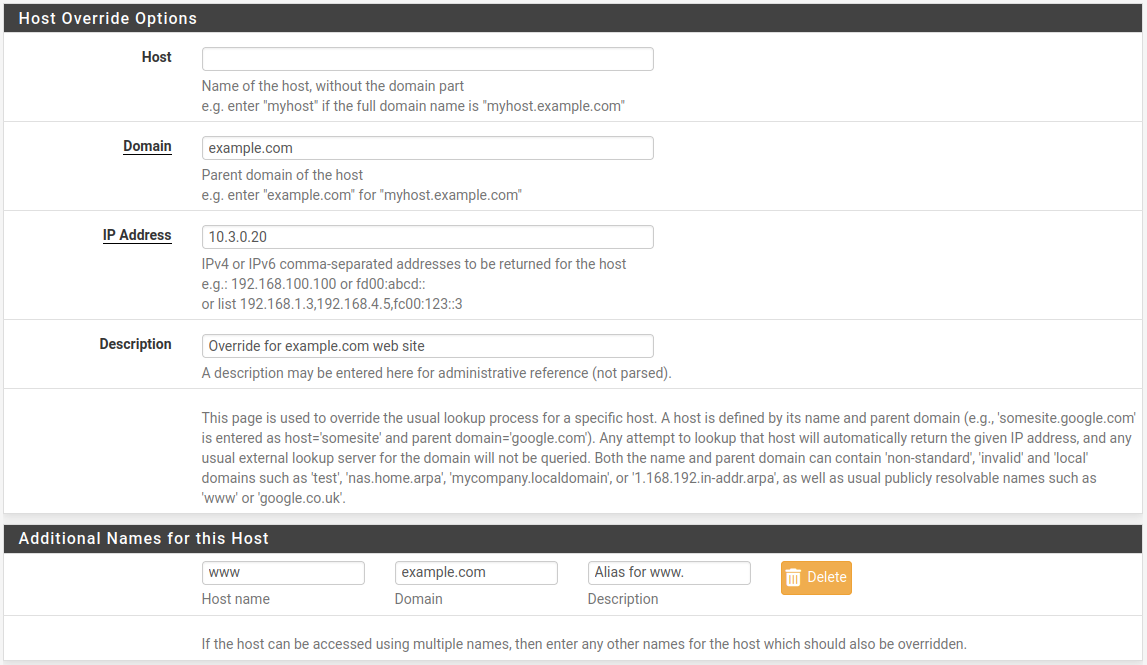
DNS Resolver Override for example.com¶
The DNS Forwarder works identically in this regard. If the DNS Forwarder is enabled instead of the DNS Resolver, add the overrides there.
An override is required for each hostname in use behind the firewall.
Internal DNS servers¶
When using a separate DNS server on an internal network, such as Microsoft Active Directory, zones must be created by the DNS server administrator for all domains hosted inside the network, along with all other records for those domains (A, CNAME, MX, etc.).
In environments running the BIND DNS server where the public DNS is hosted on the same server as the private DNS, BIND’s views feature is used to resolve DNS differently for internal hosts than external ones. Other DNS servers may offer similar functionality. Check their documentation for information.