1:1 NAT¶
1:1 NAT (pronounced “one-to-one NAT”) maps one external IP address to one internal IP address. This usually maps a public IP address on a WAN type interface to a private IP address on a LAN type interface.
For outbound packets, 1:1 NAT rules translate the source address of all packets originating from an internal address to an external address as those packets exit the interface defined in the rule.
For inbound packets, 1:1 NAT rules translate the destination address of all packets initiated from external hosts (e.g. from the Internet) destined for the external IP address on the rule interface to the private IP address on the rule. The firewall then evaluates those packets against the firewall ruleset on the external interface (e.g. WAN). If firewall rules on the external interface permit packets matching a target of the internal IP address, those packets will pass to the internal IP address.
1:1 NAT rules can also translate entire subnets provided the subnets are the same size and align on proper subnet boundaries.
1:1 NAT rules do not change ports on packets, they remain static. For example, on outbound connections, 1:1 NAT rules preserve the source ports used by the local host, similar to using Static Port on outbound NAT rules.
1:1 NAT Risks¶
The risks of 1:1 NAT are essentially the same as the risks for port forwarding if firewall rules on the external interface pass packets, since they both may potentially admit harmful content into the local network.
There is some added risk with 1:1 NAT rules in that firewall rule mistakes can have more severe consequences. With port forward rules, packets are limited by constraints within the port forward rule and the firewall rule. If a port forward rule opens TCP port 80, then an allow all rule on WAN still only permits packets with a destination of TCP port 80 on that internal host. With 1:1 NAT rules in place and an allow all firewall rule on WAN, that rule exposes everything on that internal host to the Internet.
In either case, misconfigurations are always a potential hazard, and this alone is not a reason to avoid 1:1 NAT rules. Keep these behaviors in mind when configuring firewall rules and avoid permitting any connections not required by internal hosts.
1:1 NAT Rule Precedence¶
For outbound packets, 1:1 NAT rules take precedence over outbound NAT rules. This allows 1:1 NAT rules to override default behaviors defined in outbound NAT rules, including automatic outbound NAT.
For inbound packets, port forward rules take precedence over 1:1 NAT rules. This allows port forwards to override 1:1 NAT rule behavior and forward specific ports to different internal targets or even the firewall itself.
1:1 NAT Rule Options¶
When adding or editing a 1:1 NAT rule under Firewall > NAT on the 1:1 tab, each rule has the following options:
- Disabled:
Controls whether this 1:1 NAT rule is active.
- No BINAT (NOT):
Excludes packets matching this 1:1 NAT rule from 1:1 NAT when packets would otherwise match another rule after this rule in the list.
- Interface:
The interface where the 1:1 NAT translation will take place, typically a WAN type interface.
The 1:1 NAT rule will only affect packets entering and exiting this specific interface. If there are multiple WAN type interfaces, nudging packets to use this interface may require static routing, policy routing, or equivalent configurations.
- Address Family:
The address family this rule will match: IPv4 or IPv6. The rule will only match and act upon packets with the selected address family.
Tip
Though 1:1 NAT rules can be used with IPv6, in most cases IPv6 Network Prefix Translation (NPt) is a better fit for translating the prefix of IPv6 packets.
- External subnet IP:
The outside IP address to which this rule will translate the Internal IP address as packets enter or exit the Interface.
This is typically a Virtual IP address on Interface, or an IP address routed to the firewall on Interface.
- Internal IP:
The local IP address this rule will translate to the External subnet IP address as packets enter or exit the Interface.
This is typically an IP address behind this firewall. The device with this address must use this firewall as its gateway directly (attached) or indirectly (via static route).
Specifying a subnet mask here will translate the entire network matching the subnet mask. For example using
x.x.x.0/24will translate anything in that subnet to its equivalent host address in the external subnet.- Destination:
An optional restriction which limits packets the 1:1 NAT rule will match. The default value is Any. This field can utilize aliases when set to Address or Alias.
When a Destination value is present, the 1:1 NAT rule will only take effect for packets from or to addresses matching the value, depending on the direction:
For outbound packets, the source must match the Internal IP address and the destination IP address must match this value.
For inbound packets, the source IP address must match this value and the destination IP address must match the External subnet IP address.
- Description:
Text describing the rule, such as its intended behavior or name of a service. The best practice is to clearly describe the purpose of the rule in this field.
The description is optional and does not affect functionality of the rule.
- NAT reflection:
Overrides global NAT reflection behavior for this rule.
- Use system default:
Respects the global NAT reflection settings.
- Enable:
Always performs NAT reflection for this rule.
- Disable:
Never performs NAT reflection for this rule.
See also
Configuring 1:1 NAT Rules¶
1:1 NAT rules are located at Firewall > NAT, on the 1:1 tab.
See also
The list of 1:1 NAT rules works the same as the list of firewall rules for management. See Introduction to the Firewall Rules screen for details.
To create a new 1:1 NAT rule:
Add a Virtual IP for the public IP address to be used for the 1:1 NAT rule as described in Virtual IP Addresses
Navigate to Firewall > NAT, 1:1 tab
Click
 Add to create a new 1:1 NAT rule at the top of the list
Add to create a new 1:1 NAT rule at the top of the listConfigure the 1:1 NAT rule as described in 1:1 NAT Rule Options
Click Save
Click Apply Changes
1:1 NAT Configuration Examples¶
This section contains example scenarios and configurations for 1:1 NAT.
Example Single IP Address 1:1 Configuration¶
This section demonstrates how to configure a 1:1 NAT rule with a single internal and external IP address.
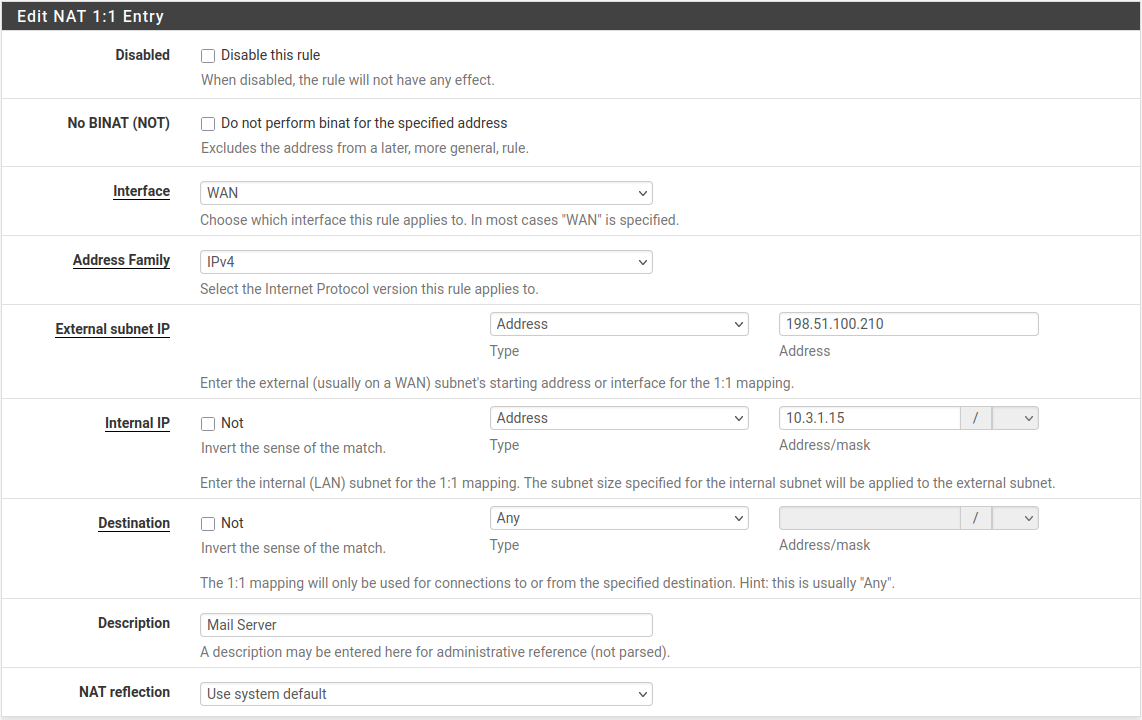
In this example, a 1:1 NAT rule will map a local mail server to a public IP
address. The external address is 198.51.100.210 which is a Virtual IP
address on the WAN interface. The mail server resides on a DMZ segment using
internal IP address 10.3.1.15.
The 1:1 NAT rule to map 198.51.100.210 to 10.3.1.15 is shown in Figure
1:1 NAT Rule.
1:1 NAT Rule¶
Example IP Address Range 1:1 Configuration¶
A 1:1 NAT rule can map multiple external IP addresses using CIDR ranges. In this example, a 1:1 NAT rule maps a /30 CIDR range of IP addresses.
See also
See CIDR Summarization for more information on summarizing networks or groups of IP addresses inside a larger subnet using CIDR notation.
External IP |
Internal IP |
|---|---|
198.51.100.64/30 |
10.3.1.64/30 |
198.51.100.64 |
10.3.1.64 |
198.51.100.65 |
10.3.1.65 |
198.51.100.66 |
10.3.1.66 |
198.51.100.67 |
10.3.1.67 |
Figure 1:1 NAT rule for /30 CIDR range shows how to configure 1:1 NAT to achieve the mapping listed in Table /30 CIDR Mapping Matching Final Octet.
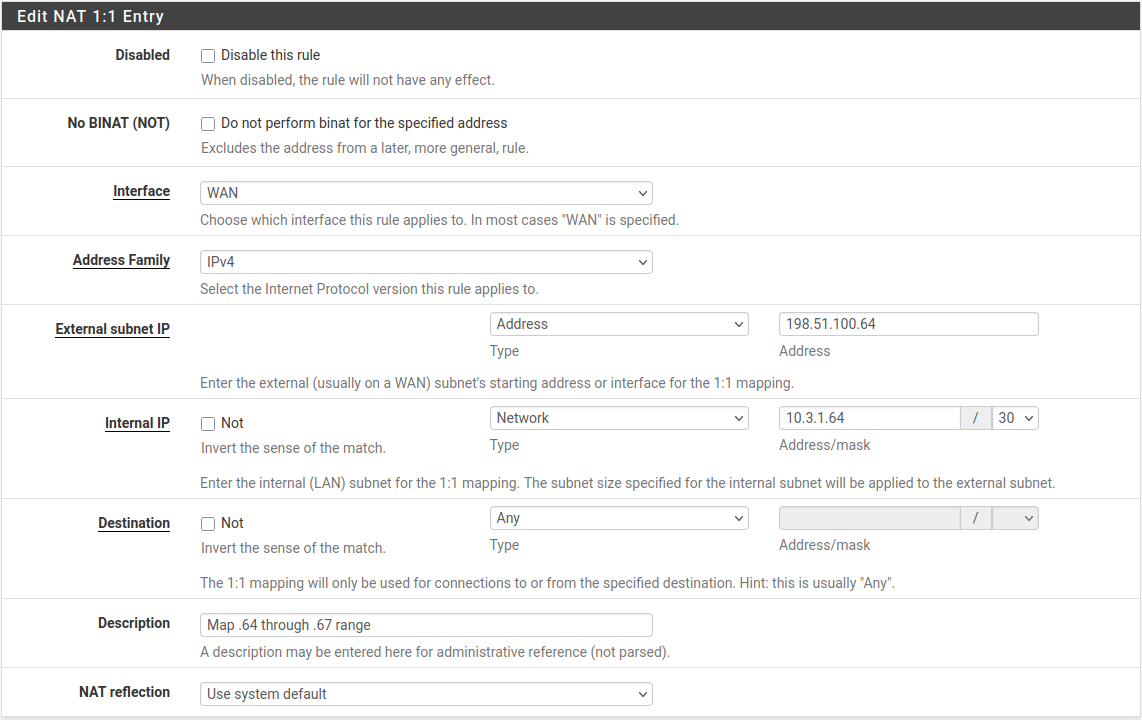
1:1 NAT rule for /30 CIDR range¶
The last octet of the IP addresses need not be the same on the inside and outside, but doing so makes it simpler to follow. For example, Table /30 CIDR Mapping Non-Matching Final Octet is also valid.
External IP |
Internal IP |
|---|---|
198.51.100.64/30 |
10.3.1.200/30 |
198.51.100.64 |
10.3.1.200 |
198.51.100.65 |
10.3.1.201 |
198.51.100.66 |
10.3.1.202 |
198.51.100.67 |
10.3.1.203 |
Choosing an addressing scheme where the last octet matches makes the layout easier to understand and hence maintain.
1:1 NAT on the WAN IP, aka “DMZ” on Consumer Gateways¶
Some consumer gateways have what they call a “DMZ” feature which forwards all ports and protocols destined to the WAN IP address to a device on the LAN. This behavior is similar to a 1:1 NAT mapping between the WAN IP address and the IP address of the internal device.
However, the manner in which these devices use the term “DMZ” is unrelated to a DMZ in formal networking terminology. In fact, it is almost the opposite. A host in a traditional network DMZ is in an isolated network away from the other LAN hosts, secured away from the Internet and LAN hosts alike. In contrast, a “DMZ” host in the consumer gateway meaning is not only on the same network as the LAN hosts, but completely exposed to incoming Internet packets with little or no protection.
pfSense® software can perform 1:1 NAT using the WAN IP address to achieve a similar effect, with the caveat that doing so leaves all services running on the firewall itself inaccessible externally. As such, 1:1 NAT rules cannot use the WAN IP address in cases where pfSense software is hosting VPNs of any type, or cases where remote users must access other local services on the firewall. In some cases, this limitation can be mitigated by using a port forward for locally hosted services.