Step 2: Initial Setup Tasks¶
Use the following diagram to support the initial setup tasks.
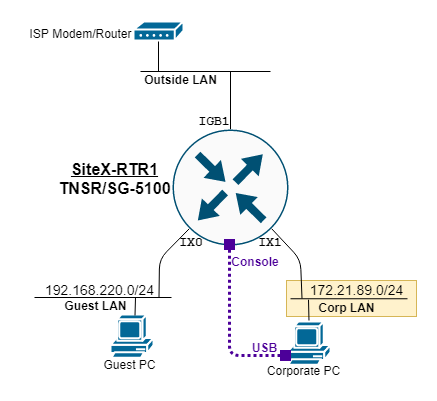
TNSR remote office setup diagram¶
Ethernet Ports Connections¶
Use RJ45 ethernet cables to connect the Netgate 5100 network ports to the WAN, CORP89, and GUEST220 networks.
Port Label |
VPP Name |
OS Name |
Assignment/name |
|---|---|---|---|
IGB0 |
n/a |
enp3s0 |
HostOS Interface |
IGB1 |
GigabitEthernet4/0/0 |
vpp1 |
WAN |
IX0 |
TenGigabitEthernet6/0/0 |
vpp2 |
GUEST220 |
IX1 |
TenGigabitEthernet6/0/1 |
vpp3 |
CORP89 |
IX2 |
TenGigabitEthernet8/0/0 |
vpp4 |
unassigned |
IX3 |
TenGigabitEthernet8/0/1 |
vpp5 |
unassigned |
HostOS Interface Notes¶
Configuration of the HostOS interface is outside the scope of this guide, see Configure the Host Interface.
Do not connect the HostOS interface to the same subnet, or broadcast domain, used by TNSR VPP interfaces as it may produce unexpected results.
More information at Host Interfaces.
Initial TNSR Setup¶
Boot up the Netgate 5100 appliance and connect to the console. Once connected, hit return to get a clear login prompt, and log in with the default TNSR user credentials.
Change Default Password¶
It is important to change the default password on the tnsr user before
proceeding:
localhost tnsr# host shell passwd
Changing password for user tnsr.
Changing password for tnsr.
(current) UNIX password:
New password:
Retype new password:
passwd: all authentication tokens updated successfully.
localhost tnsr#
Set Hostname¶
Set the TNSR hostname and save the configuration:
localhost tnsr# config
localhost tnsr(config)# system name sitex-rtr1
sitex-rtr1 tnsr(config)# db copy running startup
sitex-rtr1 tnsr(config)# exit
sitex-rtr1 tnsr#
Configure Dataplane¶
Enable selected network and crypto devices on the TNSR dataplane and then restart it, as shown in the config fragment below:
dataplane dpdk dev 0000:04:00.0 network name WAN
dataplane dpdk dev 0000:06:00.0 network name GUEST220
dataplane dpdk dev 0000:06:00.1 network name CORP89
dataplane dpdk dev 0000:01:00.0 crypto
#
service dataplane restart
Note
When enabling the crypto hardware device (QAT) on the console port or during system boot, it is normal for a number of log messages to display as it initializes, these can typically be ignored. For example:
[ 836.798096] c3xxxvf 0000:01:01.4: enabling device (0000 -> 0002)
[ 836.804235] DMAR: 64bit 0000:01:01.4 uses identity mapping
[ 836.839343] c3xxxvf 0000:01:01.0: Failed to register crypto algs
[ 836.859227] c3xxxvf: probe of 0000:01:01.0 failed with error -14
[ 836.865313] c3xxxvf 0000:01:01.1: enabling device (0000 -> 0002)
[ 836.871718] DMAR: 64bit 0000:01:01.1 uses identity mapping
[ 836.877853] c3xxxvf 0000:01:01.4: Failed to register crypto algs
[ 836.897244] c3xxxvf: probe of 0000:01:01.4 failed with error -14
Inspect an interface with the show interface command. As seen below, the
WAN interface is still in Admin down state, no IP address is assigned,
and no packets have been seen.
sitex-rtr1 tnsr(config)# show interface WAN
Interface: WAN
Admin status: down
Link down, link-speed unknown, unknown duplex
Link MTU: 1500 bytes
MAC address: 00:90:0b:7a:8a:68
VRF: default
Rx-queues:
queue-id 0 : cpu-id 2 : rx-mode polling
counters:
received: 0 bytes, 0 packets, 0 errors
transmitted: 0 bytes, 0 packets, 0 errors
protocols: 0 IPv4, 0 IPv6
Save and Reboot¶
Save the configuration:
db copy running startup
And then reboot:
reboot now
Watch the console logs as the system boots up, then log in as the tnsr user
with the new password that was set earlier.