Static Routes¶
Static routes are used when hosts or networks are reachable through a router other than the default gateway. The firewall knows about the networks directly attached to it, and it reaches all other networks as directed by the routing table. In networks where an internal router connects additional internal subnets, a static route must be defined for those networks to be reachable.
Note
The routers through which these other networks are reached must first be added as gateways. See Gateways for information on adding gateways.
Static routes are managed at System > Routing on the Routes tab.
Static Route Configuration¶
When adding or editing a static route, the following options are available:
- Destination Network:
The network and subnet mask reachable using this route. This may be an IPv4 address (subnet ID), IPv6 prefix, or an alias.
Warning
When editing an alias which is used by a static route, the firewall makes changes to the routing table to reflect the new alias content as soon as the alias is saved. The firewall does not wait for the user to click Apply Changes in this circumstance.
- Gateway:
The router through which this network is reached.
- Disabled:
Check if the static route should not be used, only defined.
- Description:
Text to describe the route, its purpose, etc.
Managing Static Routes¶
To add a route:
Navigate to System > Routing on the Routes tab
Click
 Add to create a new static route
Add to create a new static routeFill in the configuration as described in Static Route Configuration
Click Save
Click Apply Changes
To manage existing routes, navigate to System > Routing on the Routes tab. On the screen there are a variety of options to manage routes:
 edits an existing route
edits an existing route creates a copy of an existing gateway
creates a copy of an existing gateway deletes a route
deletes a route disables an active route
disables an active route enables a disabled route
enables a disabled route
Example Static Route¶
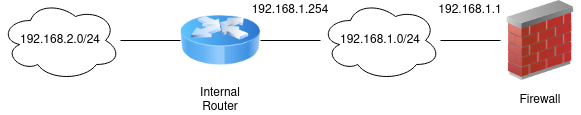
Figure Static Routes illustrates a scenario where a static route is required.
Static Routes¶
Because the 192.168.2.0/24 network in Figure Static Routes is
not on an interface directly connected to the firewall, a static route is
required for the firewall to know how to reach that network. Figure
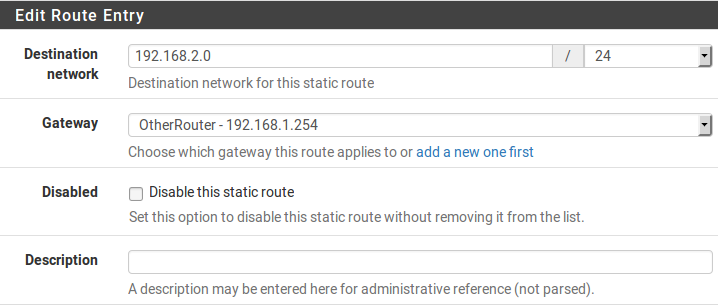
Static Route Configuration shows the appropriate static route for
the above diagram. As mentioned earlier, before a static route may be added a
gateway must first be defined.
Static Route Configuration¶
LAN firewall rules must allow traffic to pass from a source of the networks reachable via static routes on LAN, and outbound NAT must also accommodate these networks.
Bypass Firewall Rules for Traffic on Same Interface¶
In some environments using static routes, traffic ends up routing asymmetrically. This means the traffic will follow a different path in one direction than the traffic flowing in the opposite direction. Take Figure Asymmetric Routing for example.
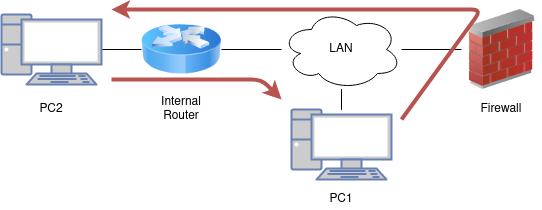
Asymmetric Routing¶
Traffic from PC1 to PC2 will go through the firewall since it is the default gateway for PC1, but traffic in the opposite direction will go directly from the router to PC1.
Since this is a stateful firewall, it must see traffic for the entire connection to be able to filter traffic properly. With asymmetric routing such as in this example, any stateful firewall will drop legitimate traffic because it cannot properly keep state without seeing traffic in both directions. This generally only affects TCP, since other protocols do not have a formal connection handshake the firewall can recognize for use in state tracking.
Note
A connection may appear to work for a short time and then stop. This can be from the firewall removing a state which doesn’t transition to a fully open state, or it may be from clients expiring an ICMP redirect.
In asymmetric routing scenarios, there is an option in the firewall GUI which can be used to prevent legitimate traffic from being dropped. The option adds firewall rules which allow all traffic between networks defined in static routes using a more permissive set of rule options and state handling. To activate this option:
Click System > Advanced
Click the Firewall/NAT tab
Check Bypass firewall rules for traffic on the same interface
Click Save
Alternatively, firewall rules may be added manually to allow similar traffic. Two rules are needed, one on the interface tab where the traffic enters (e.g. LAN) and another on the Floating tab:
Navigate to Firewall > Rules
Click the tab for the interface where the traffic will enter (e.g. LAN)
Click
 Add to add a new rule to the top of the list
Add to add a new rule to the top of the listUse the following settings:
- Protocol:
TCP
- Source:
The local systems utilizing the static route (e.g. LAN Net)
- Destination:
The network on the other end of the route
- TCP Flags:
Check Any flags (Under Advanced Features)
- State Type:
Sloppy State (Under Advanced Features)
Click Save
Click the Floating tab
Click
 Add to add a new rule to the top of the list
Add to add a new rule to the top of the listUse the following settings:
- Interface:
The interface where the traffic originated (e.g. LAN)
- Direction:
Out
- Protocol:
TCP
- Source:
The local systems utilizing the static route (e.g. LAN Net)
- Destination:
The network on the other end of the route
- TCP Flags:
Check Any flags (Under Advanced Features)
- State Type:
Sloppy State (Under Advanced Features)
Click Save
If additional traffic from other sources or destinations is shown as blocked in the firewall logs with TCP flags such as “TCP:SA” or “TCP:PA”, the rules may be adjusted or copied to match that traffic as well.
Note
If filtering of traffic between statically routed subnets is required, it must be done on the router and not the firewall since the firewall is not in a position on the network where it can effectively control that traffic.
See also
ICMP Redirects¶
When a device sends a packet to its default gateway, and the gateway knows the sender can reach the destination network via a more direct route, it will send an ICMP redirect message in response and forward the packet as configured. The ICMP redirect causes a route for that destination to be temporarily added to the routing table of the sending device, and the device will subsequently use that more direct route to reach that destination.
This will only work if the client OS is configured to permit ICMP redirects, which is typically the case by default.
ICMP redirects are common when static routes are present which point to a router on the same interface as client PCs and other network devices. The asymmetric routing diagram from the previous section is an example of this.
ICMP redirects have a mostly undeserved bad reputation from some in the security community because they allow modification of a client routing table. However, they are not the risk that some imply, as to be accepted, the ICMP redirect message must include the first 8 bytes of data from the original datagram. A host in a position to see that data and hence be able to successfully forge illicit ICMP redirects is in a position to accomplish the same end result in multiple other ways.