OpenVPN Firewall Rules¶
Permitting traffic to the OpenVPN server¶
A firewall rule must permit traffic to the OpenVPN server or clients will not be able to connect. Add a rule as follows:
Navigate to Firewall > Rules, WAN tab
Click
 to create a new rule at the top of the list
to create a new rule at the top of the listSet the options as follows:
- Protocol:
UDP
- Source:
any
- Destination:
WAN Address
- Destination port:
1194, or whichever port the server is using to listen- Description:
Allow traffic to OpenVPN Server
Click Save
Click Apply changes
This rule is depicted in Figure OpenVPN Server WAN Rule.
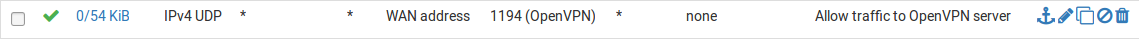
OpenVPN Server WAN Rule¶
If the client source addresses are known and do not change, then the source of the rule could be altered to limit traffic from only those clients. This is more secure than leaving the server exposed to the entire Internet, but that is often necessary to accommodate clients with dynamic IP addresses, roaming clients, and so on. The risk of leaving the service exposed with most OpenVPN configurations is minimal, especially in cases where OpenVPN servers utilize TLS Authentication. With certificate-based authentication there is less risk of compromise than password-based solutions which can be susceptible to brute forcing. This presumes a lack of security holes in OpenVPN itself, which to date has a solid security track record.
Allowing traffic over OpenVPN Tunnels¶
By default, all traffic is blocked from entering OpenVPN tunnels. To allow traffic from remote OpenVPN hosts to make connections to resources on the local side through the VPN, add firewall rules under Firewall > Rules, on the OpenVPN tab.
As with other aspects of the firewall these rules only match traffic coming into the firewall from remote sources, they do not control traffic leaving from this firewall. Craft the rules accordingly.
Add an OpenVPN rule which passes all traffic as follows:
Navigate to Firewall > Rules, OpenVPN tab
Click
 to create a new rule at the top of the list
to create a new rule at the top of the listSet the options as follows:
- Protocol:
any
- Source:
any
- Destination:
any
- Description:
Allow all on OpenVPN
Click Save
Click Apply changes
To limit the traffic to only specific sources and destinations, adjust the rule(s) as needed. A strict ruleset is more secure, but more difficult to create.
Tip
Rules on the OpenVPN tab apply to all OpenVPN server and client instances. The OpenVPN interface may also be assigned (Assigning OpenVPN Interfaces) in which case there will be a separate firewall rule tab for that VPN, upon which rules can pass traffic for that specific VPN.
Rules on assigned OpenVPN interface tabs are processed after rules on the OpenVPN tab. Rules on the OpenVPN tab must not pass or block traffic too broadly or the firewall will stop processing before it gets to the assigned interface tab rules.