Testing Connectivity¶
Verify that the IPsec tunnels are functioning by attempting to ping the “inside tunnel addresses” of the VPC side of the tunnel by navigating to Firewall > Virtual IP. There should be two virtual IP addresses configured that have Descriptions like “Inside address for tunnel to <remote IP address>”.
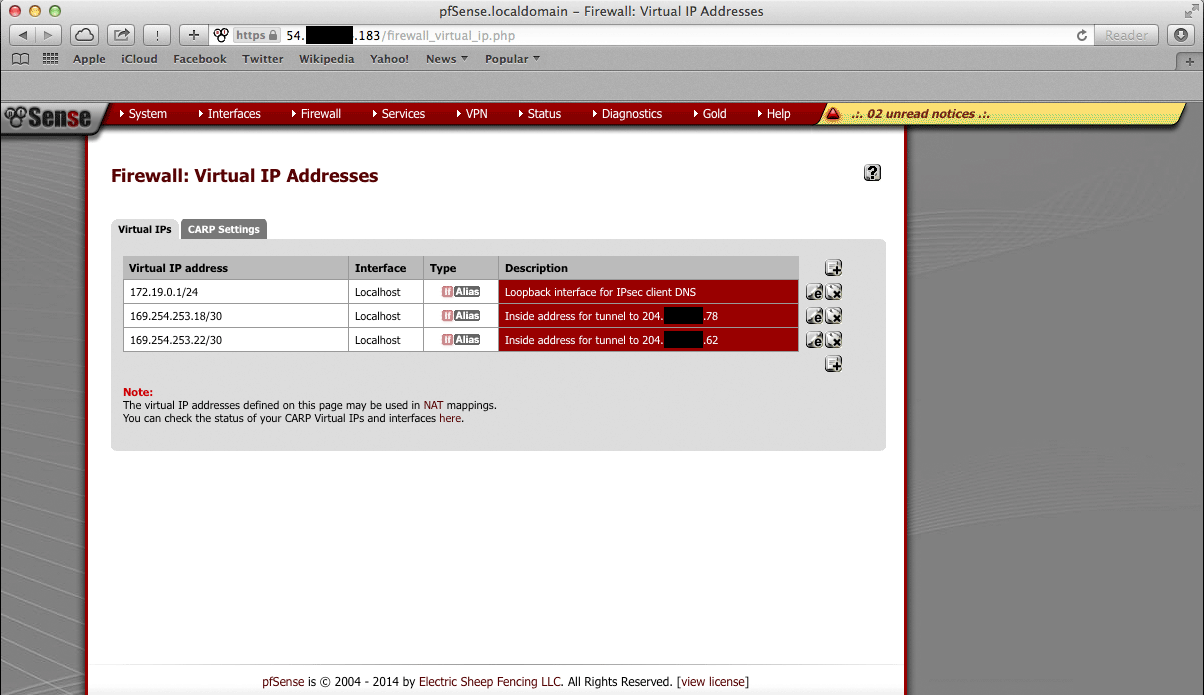
Amazon provides inside addresses for each end of the tunnel in a /30 subnet
in IPv4 link local address space (169.254.x.y). Typically, the first usable
address in the /30 is the inside address for the VPC end of the tunnel and
the other usable address is the inside address for the local end of the tunnel.
Ping from one of the virtual IP addresses configured on the pfSense Plus
instance to the IP address that is one less (for example, if the virtual IP
address were 169.254.253.22, ping from 169.254.253.22 to
169.254.253.21), that checks whether the other end of the tunnel is
responding and whether the tunnel is functioning properly.
Note
It sometimes takes a few minutes for the tunnels to begin working after the configuration wizard completes.
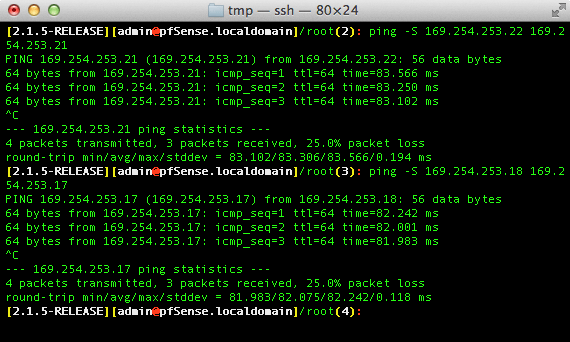
To ping, log into the pfSense Plus instance via SSH and execute ping from
a shell prompt. For the previous example of 169.254.253.22, the proper
syntax is:
ping -S 169.254.253.22 169.254.253.21
When pinging from a shell prompt, it is possible to leave the command running indefinitely and interrupt it there is a response.
It is also possible to ping via the Diagnostics > Ping page by selecting the appropriate source address and entering the remote tunnel inside address in the Host field. This will only send a limited number of ping packets, so it may be necessary to repeat this a few times.