Interface Groups¶
Unlike the other interfaces in this chapter, an Interface Group is not a type of interface that can be assigned. Interface groups are used to apply firewall or NAT rules to a set of interfaces on a common tab. If this concept is unfamiliar, consider how the firewall rules for OpenVPN, the PPPoE server, or L2TP server work. There are multiple interfaces in the underlying OS, but the rules for all of them are managed on a single tab for each type.
If many interfaces of a similar function are present on the firewall that need practically identical rules, an interface group may be created to add rules to all the interfaces at the same time. Interfaces can still have their own individual rules, which are processed after the group rules.
Interface Group Options¶
When creating or editing an Interface Group, the following options are available:
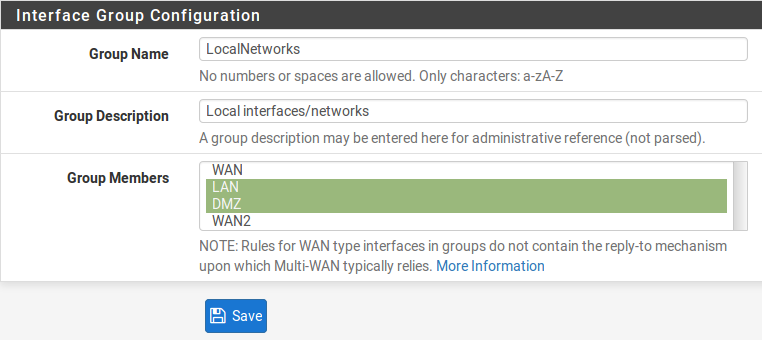
- Group Name:
The name of the interface group. Has the same restrictions as the name of an interface. The name may only contain upper and lowercase letters, no numbers, spaces, or special characters.
- Group Description:
An optional text description for reference.
- Group Members:
A multi-select list of assigned interfaces on the firewall from which group members can be added. Add interfaces to the group by selecting them with Ctrl-click (PC) or cmd-click (MAC).
Creating an Interface Group¶
To create an interface group:
Navigate to Interfaces > Assignments, Interface Groups tab
Click
 Add to create a new group
Add to create a new groupFill in the options as described in Interface Group Options
Click Save
Add Interface Group¶
Using an Interface Group¶
Interface groups each have an individual tab under Firewall > Rules to manage their rules. Figure Interface Group Firewall Rules Tab shows the firewall rule tab for the group defined in figure Add Interface Group
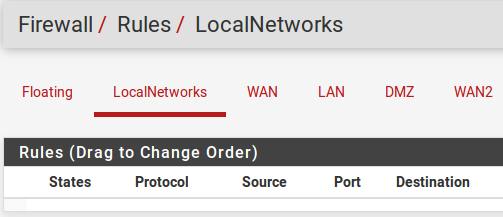
Interface Group Firewall Rules Tab¶
See also
Configuring Firewall Rules for information on managing firewall rules.
Group Rule Processing Order¶
The rule processing order for user rules is:
Floating rules
Interface group rules
Rules on the interface directly
For example, if a rule on the group tab matches a connection, the interface tab rules will not be consulted. Similarly, if a floating rule with Quick set matched a connection, the interface group rules will not be consulted.
The processing order prevents some combination of rules that otherwise might be a good fit. For example, if a general blocking rule is present on the group, a rule on a specific interface cannot override it. Same with a pass rule, a specific interface rule cannot block traffic passed on a group tab rule.
Use with WAN Interfaces¶
The best practice is to not use interface groups with multiple WANs. Doing so
may appear to be convenient, but the group rules do not receive the same
treatment as actual WAN tab rules. For example, rules on a tab for a WAN-type
interface will receive reply-to which allows PF to return traffic back via
the interface from which it entered. Group tab rules do not receive reply-to
which effectively means that the group rules only function as expected on the
WAN with the default gateway.