Configuring IPsec IKEv2 Remote Access VPN Clients on Ubuntu¶
This document demonstrates how to configure an IKEv2 connection on Ubuntu. This procedure was performed on Linux Mint 21.3, but the procedure is identical on most recent similar distributions.
Prerequisites¶
Before starting:
Setup TNSR as an IKEv2 server as described in either IPsec Remote Access VPN using IKEv2 with EAP-TLS or IPsec Remote Access VPN using IKEv2 with EAP-RADIUS.
Install
network-manager-strongswanandlibcharon-extra-pluginsusingaptor a similar mechanismExport the CA certificate (EAP-TLS or EAP-RADIUS), user certificate (EAP-TLS), and user key (EAP-TLS) as separate files and copy them to the Ubuntu client
Warning
The Network Manager configuration window for IKEv2 IPsec is quite tall and if the screen height is less than 900 pixels it may not be possible to configure and save the VPN easily. Behavior may vary with different desktop environments, window managers, etc.
Configuration¶
The configuration varies slightly depending on the server configuration.
EAP-TLS¶
Click the Network Manager icon in the notification tray by the clock
Note
The icon varies depending on the type of network in use.
Click Network Connections
Click Add
Select IPsec/IKEv2 (strongswan) under VPN as shown in Adding an IKEv2 VPN on Ubuntu
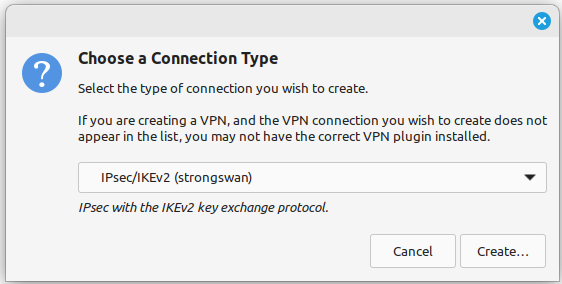
Adding an IKEv2 VPN on Ubuntu¶
Note
If the option is not present, double check that
network-manager-strongswanis installed.Click Create
Select the VPN Tab
Set the fields as follows:
- Connection Name
A name for this connection,
TNSR IKEv2 EAP-TLS.- Address
The FQDN or IP address of TNSR, e.g.
tnsr.example.com.- Certificate
Click the field and browse to find the IPsec CA Certificate file.
- Identity
Set to match a SAN of the server cert, or leave blank to use the Address value.
- Authentication
EAP-TLS
- Certificate
Certificate/Private Key
- Certificate File
Click the field and browse to find the user certificate file.
- Private Key
Click the field and browse to find the user private key file.
- Identity
Set to match the common name of the certificate (e.g.
ipsec-myuser)- Password
Click the icon at the end of the field and set to The password is not required.
Select the Options tab at the bottom of the window
Set the fields as follows:
- Request an Inner IP Address
Checked
Select the Algorithms tab at the bottom of the window
Set the fields as follows:
- Enable Custom algorithm proposals
Checked
- IKE
Set to match the TNSR config in strongSwan format, e.g.
aes256gcm128-sha256-modp2048.- ESP
Set to match the TNSR config in strongSwan format, e.g.
aes256gcm128-modp2048.
See also
For a list of algorithms and their equivalent strings in strongSwan, see the strongSwan document on IKEv2 Cipher Suites.
Compare the settings to those shown in figures Ubuntu VPN Client Settings for EAP-TLS and Ubuntu VPN Client Algorithm Settings
Click Save
Click Close
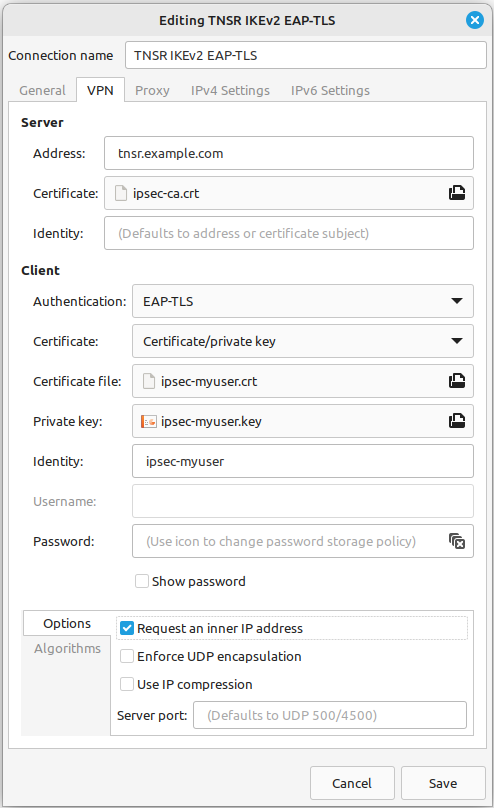
Ubuntu VPN Client Settings for EAP-TLS¶
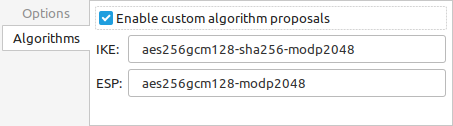
Ubuntu VPN Client Algorithm Settings¶
EAP-RADIUS¶
Click the Network Manager icon in the notification tray by the clock
Note
The icon varies depending on the type of network in use.
Click Network Connections
Click Add
Select IPsec/IKEv2 (strongswan) under VPN as shown in Adding an IKEv2 VPN on Ubuntu

Adding an IKEv2 VPN on Ubuntu¶
Note
If the option is not present, double check that
network-manager-strongswanis installed.Click Create
Select the VPN Tab
Set the fields as follows:
- Connection Name
A name for this connection,
TNSR IKEv2 EAP-RADIUS.- Address
The FQDN or IP address of TNSR, e.g.
tnsr.example.com.- Certificate
Click the field and browse to find the IPsec CA Certificate file.
- Identity
Set to match a SAN of the server cert, or leave blank to use the Address value.
- Authentication
EAP (Username/Password)
- Username
Enter the RADIUS username.
- Password
Click the icon at the end of the field and set to Ask for this password every time.
Note
Although the client allows saving the password, the best practice is to not store credentials in this manner.
Select the Options tab at the bottom of the window
Set the fields as follows:
- Request an Inner IP Address
Checked
Select the Algorithms tab at the bottom of the window
Set the fields as follows:
- Enable Custom algorithm proposals
Checked
- IKE
Set to match the TNSR config in strongSwan format, e.g.
aes256gcm128-sha256-modp2048.- ESP
Set to match the TNSR config in strongSwan format, e.g.
aes256gcm128-modp2048.
See also
For a list of algorithms and their equivalent strings in strongSwan, see the strongSwan document on IKEv2 Cipher Suites.
Compare the settings to those shown in figures Ubuntu VPN Client Settings for EAP-RADIUS and Ubuntu VPN Client Algorithm Settings
Click Save
Click Close
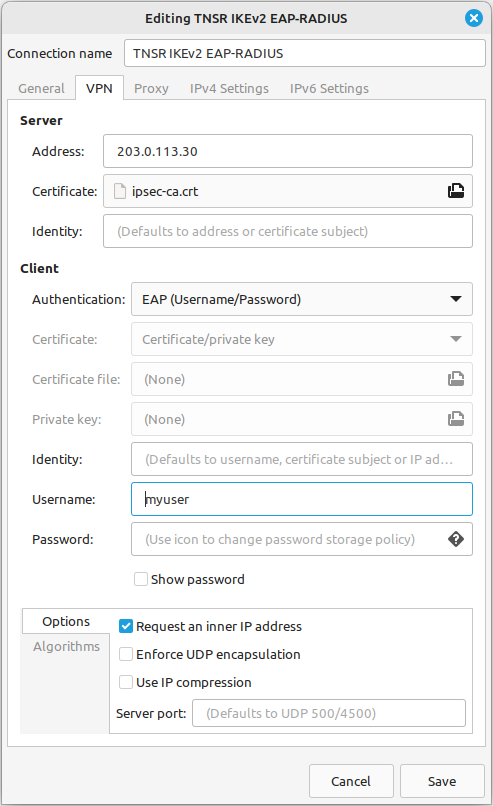
Ubuntu VPN Client Settings for EAP-RADIUS¶

Ubuntu VPN Client Algorithm Settings¶
Split Tunneling¶
The Ubuntu IPsec client will automatically respect the traffic selectors configured on the server. The client does not require any manual adjustments.
If there are no traffic selectors on the server, the client will send all of its traffic, including Internet traffic, across the VPN.
The client includes options to override this behavior on the IPv4 and IPv6 Settings tabs under the Routes button.
Connecting and Disconnecting¶
To Connect:
Click the Network Manager icon
Click the VPN Name or click VPN Connections to move the slider to the On (1) position
To Disconnect:
Click the Network Manager icon
Click VPN Connections to move the slider to the Off (0) position