Tip
This is the documentation for the 23.11 version. Looking for the documentation of the latest version? Have a look here.
GRE ERSPAN Example Use Case¶
Encapsulated Remote Switched Port Analyzer (ERSPAN) is a type of GRE tunnel which allows a remote Intrusion Detection System (IDS) or similar packet inspection device to receive copies of packets from a local interface. This operates similar to a local mirror or span port on a switch, but in a remote capacity.
A typical use case for this is central packet inspection or a case where a remote site has plenty of bandwidth available, but no suitable local hardware for inspecting packets.
On TNSR, this is accomplished by configuring an ERSPAN GRE tunnel and then configuring a span to link the ERSPAN tunnel a local interface. From that point on, a copy of every packet on the interface being spanned is sent across GRE.
Note
The receiving end does not need to support ERSPAN, a standard GRE tunnel will suffice.
See also
In environments which do not allow GRE traffic, such as Azure, VXLAN interfaces may be used instead. See VXLAN SPAN Example.
Example Scenario¶
In this example, copies of packets from a local TNSR interface will be copied to a remote IDS for inspection.
Item |
Value |
|---|---|
Local Server: |
172.29.193.47/24 |
TNSR Local Interface: |
VirtualFunctionEthernet0/6/0 |
TNSR Local Address: |
172.29.193.60/24 |
TNSR Internet Interface: |
VirtualFunctionEthernet0/7/0 |
TNSR Internet Address: |
172.29.194.142/24 |
IDS Address: |
172.29.194.90/24 |
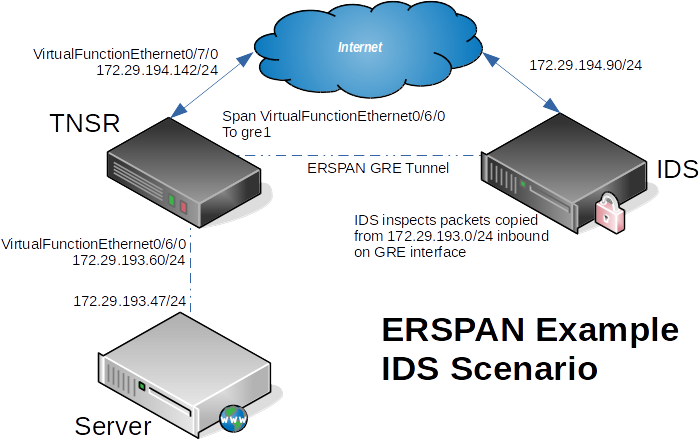
ERSPAN Example¶
TNSR Configuration¶
First, there is the basic interface configuration of TNSR to handle IP connectivity:
tnsr(config)# interface VirtualFunctionEthernet0/6/0
tnsr(config-interface)# ip address 172.29.193.160/24
tnsr(config-interface)# description Local
tnsr(config-interface)# enable
tnsr(config-interface)# exit
tnsr(config)# interface VirtualFunctionEthernet0/7/0
tnsr(config-interface)# ip address 172.29.194.142/24
tnsr(config-interface)# description Internet
tnsr(config-interface)# enable
tnsr(config-interface)# exit
Next, configure the GRE tunnel on TNSR:
tnsr(config)# gre gre1
tnsr(config-gre)# destination 172.29.194.90
tnsr(config-gre)# source 172.29.194.142
tnsr(config-gre)# tunnel-type erspan session-id 1
tnsr(config-gre)# instance 1
tnsr(config-gre)# exit
tnsr(config)# interface gre1
tnsr(config-interface)# enable
tnsr(config-interface)# exit
Finally, configure a SPAN that ties the local interface to the GRE interface:
tnsr(config)# span VirtualFunctionEthernet0/6/0
tnsr(config-span)# onto gre1 hw both
tnsr(config-span)# exit
Server Configuration¶
No configuration is necessary on the server. Any packet it sends which flows through TNSR will automatically be copied across the ERSPAN tunnel to the IDS.
IDS Configuration¶
The IDS must support GRE interfaces and also must support inspecting packets on GRE interfaces. The IDS does not need to explicitly support ERSPAN to receive copies of packets from TNSR.
At a minimum, take the following steps on the IDS:
Configure a GRE tunnel between the IDS and TNSR, it does not need to have an address internal to the GRE tunnel.
Configure the IDS software to inspect packets on the GRE interface