Tip
This is the documentation for the 24.06 version. Looking for the documentation of the latest version? Have a look here.
Step 5: Corporate VPN with IPsec Tunnel¶
An IPsec IKEv2 VPN tunnel is configured between the remote office and the VPN head end at the corporate office.
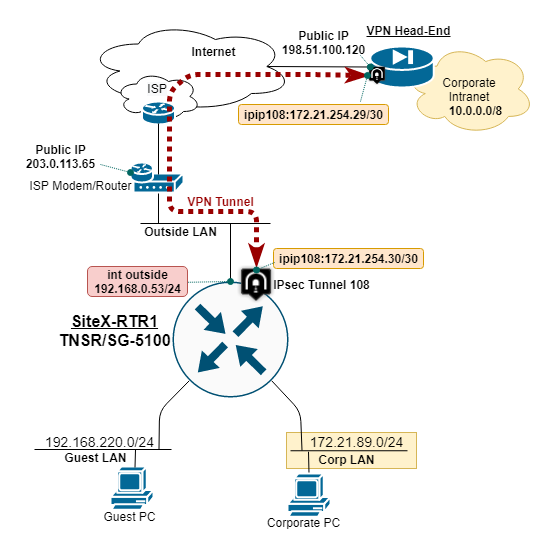
TNSR remote office IPsec VPN diagram¶
IPsec Deployment Parameters¶
The IPsec tunnel is built with the following parameters:
IP address of each tunnel endpoint, both the remote office and VPN head end.
Local and Remote Identity and Pre-Shared Key (PSK).
Compatible Phase 1 Proposal: AES256, SHA256, DH14.
Compatible Phase 2 Proposal: AES128GCM16, DH14.
IP address assigned to the tunnel interface, typically a /30 subnet.
IP route to direct corporate traffic over IPsec tunnel via next-hop IP.
The parameters for this deployment were captured at IPsec VPN Tunnel Parameters.
In this example, the Remote Office TNSR is behind NAT on the ISP cable mode, and using a Private IP address.
TNSR WAN IP: 192.168.0.53
TNSR Public IP: 203.0.113.65
The NAT-T feature of TNSR will recognize there is a NAT device translation in the path (traversal) and float the VPN tunnel traffic to UDP port 4500. This ensures the external NAT devices does not block the IPsec (VPN) traffic.
TNSR NAT Inbound Forwarding of IKE and ESP Packets¶
By default, TNSR will block inbound traffic on the WAN NAT inteface. To
permit the IPsec traffic, add nat static mappings to forward the inbound
IPsec traffic to TNSR.
nat static mapping udp local 192.168.0.53 500 external WAN 500
nat static mapping udp local 192.168.0.53 4500 external WAN 4500
Note
These accessible UDP ports should be protected by an ACL, to includes source addresses in the rules when possible.
Configure the IPIP Tunnel¶
Configure the IPIP tunnel which will carry traffic inside the IPsec tunnel:
tunnel ipip 108
source ipv4 address 192.168.0.53
destination ipv4 address 198.51.100.120
exit
Configure IPsec Tunnel¶
Configure the IPsec tunnel on the remote office TNSR:
ipsec tunnel 108
enable
crypto config-type ike
crypto ike
version 2
lifetime 28800
proposal 1
encryption aes256
integrity sha256
group modp2048
exit
identity local
type address
value 203.0.113.65
exit
identity remote
type address
value 198.51.100.120
exit
authentication local
round 1
psk AD78PPQMP00
exit
exit
authentication remote
round 1
psk AD78PPQMP00
exit
exit
child 1
lifetime 3600
proposal 1
encryption aes128gcm16
no integrity
group modp2048
exit
exit
exit
exit
#
Configure IP Tunnel Address and MTU¶
Configure a static IP address on the IPsec tunnel, and set the ip mtu to account for IPsec overhead:
interface ipip108
ip address 172.21.254.30/30
mtu 1400
enable
exit
#
To test, ping the other end of the IPsec tunnel with:
ping 172.21.254.29 source 172.21.254.30 count 5
Use this test to confirm if the IPsec Tunnel is load-bearing.
Configure IP Route to Corporate¶
Configure a static IP route to direct corporate traffic over the IPsec tunnel via the next-hop on the IPsec tunnel:
route table default
route 10.0.0.0/8
next-hop 0 via 172.21.254.29
exit
exit
#
Save changes:
configuration copy running startup