Assigning OpenVPN Interfaces¶
Assigning an OpenVPN interface as an OPT interface allows the firewall to perform complex NAT, policy routing, and tunnel-specific filtering.
Benefits of assigning an OpenVPN instance as an interface include:
Adds a firewall tab under Firewall > Rules
Adds
reply-toto rules on the VPN interface tab to help with return routingAdds a gateway entry for the far side of the VPN for policy routing
Allows the interface to be selected elsewhere in the GUI and packages for binding services and other tasks
Allows fine-grained control of port forwards and outbound NAT for the VPN
Note
This does not change the functionality of OpenVPN, only how the firewall treats the interface.
Interface assignment and configuration¶
Navigate to System > Routing
Set the Default gateway options to a specific gateway or group, as long as they are not left at Automatic (Managing the Default Gateway)
Warning
If the default gateway remains set to Automatic the firewall may end up using the OpenVPN interface as the default gateway, which is unlikely to be the desired outcome.
Navigate to Interfaces > Assignments
Set the Available network ports field to the appropriate
ovpnsorovpncinterfaceThe GUI prints description of the VPN next to the interface name for reference.
Click
 Add to create the interface assignment
Add to create the interface assignmentThe firewall assigns the interface an automatic
OPTxinterface name (e.g.OPT1)Figure Assign OpenVPN Interface shows
ovpns1assigned as OPT1.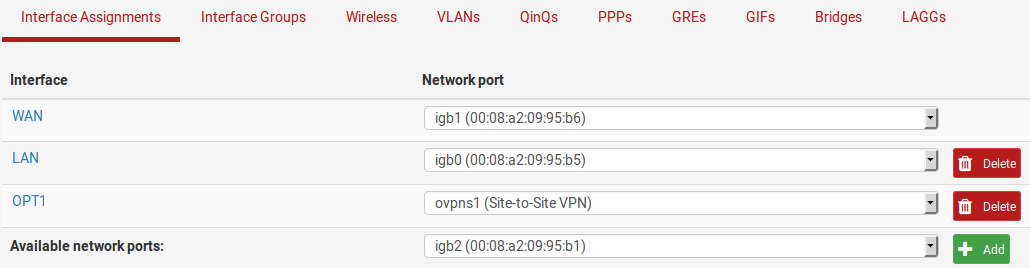
Assign OpenVPN Interface¶
Navigate to the interface configuration page, Interfaces > OPTx
Check Enable
Enter an appropriate Description which will become the interface name (e.g.
VPNServer)Click Save
Click Apply Changes
Navigate to VPN > OpenVPN and edit the newly assigned instance using the appropriate tab (Servers or Clients)
Do not make any changes
Click Save to refresh the VPN configuration and restart its process
Warning
This reinitialization is necessary for the VPN to recover from the assignment process.
Filtering with OpenVPN¶
When an OpenVPN interface is assigned the GUI contains a tab for the interface under Firewall > Rules dedicated to the specific VPN instance.
Rules on this tab govern traffic coming in from the remote side of the VPN and
these rules also get the reply-to keyword which ensures traffic entering
this VPN interface will exit back out the same interface. This can help with
advanced NAT and routing configuration scenarios.
Note
Rules on assigned interface tabs are processed after rules on the OpenVPN tab. To match the rules on an assigned VPN tab, the traffic must not match any rules on the OpenVPN tab. Remove any “Allow All” or “Block all” style rules from the OpenVPN tab and craft more specific rules instead.
See also
Policy Routing with OpenVPN¶
The firewall automatically creates dynamic gateways for assigned and enabled OpenVPN interfaces. These gateways can be found under System > Routing, on the Gateways tab.
The firewall will create both IPv4 and IPv6 gateways by default but the Gateway creation option on OpenVPN instances can limit this behavior to either IPv4 or IPv6.
Firewall rules can use these gateways to direct traffic into the VPN using the Gateway field on LAN or other internal interface rules. These gateways can also be included in gateway groups for failover or load balancing.
Reaching Internet sites through the VPN may require more configuration. Either outbound NAT must be performed on the VPN interface before it leaves the firewall (e.g. For VPN services such as PIA, StrongVPN and similar) or the NAT must be performed on the remote side before it reaches the Internet. To perform outbound NAT on this firewall, switch to Hybrid or Manual outbound NAT mode and add outbound NAT rules on the assigned OpenVPN interface matching the appropriate traffic sources.
See also
Warning
Do not use this automatic gateway for static routes, use the Remote Network field in the VPN configuration instead. Automatic gateways for assigned OpenVPN interfaces do not work properly for static routes.
NAT with OpenVPN¶
Assigned OpenVPN interfaces can utilize any type of NAT rules. This is useful when connecting two conflicting subnets or for making NAT rules specific to this a single VPN connection (outbound NAT, port forwards, or 1:1 NAT)