Troubleshooting Blocked Log Entries for Legitimate Connection Packets¶
Sometimes log entries will be present that appear to be blocking legitimate traffic, while labeled with the “Default deny” or even sometimes a pass rule. There are several possible causes for this behavior.
Out-of-State Web Server Packets¶
The most common example is seeing a connection blocked involving a web server.
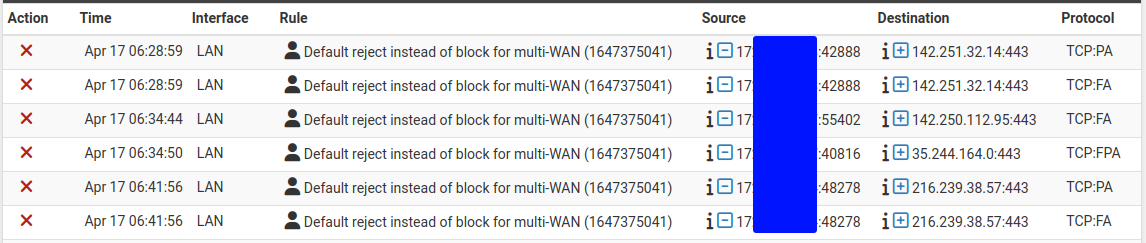
Log entries for blocked out-of-state TCP packets¶
This is likely due to a TCP FIN packet arriving after firewall has removed the connection state. This happens because on occasion a packet will be lost, and the retransmits will be blocked because the firewall has already closed the connection. Another possible reason for the messages is if a packet arrived too slowly and was outside its expected arrival window. It can also happen when web servers attempt to reuse connections.
In each case, the log entries are harmless and do not indicate a blocked connection. All stateful firewalls do this, though some do not generate log messages for this blocked traffic even if all blocked traffic is logged.
These blocked packets will occur even if rules exist which look as though they should match the traffic, such as an “Allow All” rule. Pass rules for TCP only allow TCP SYN packets to create a state. These rules assume TCP traffic with other flags will either be part of an existing state in the state table, or packets with spoofed TCP flags.
See also
Packets with IP Options¶
PF will drop packets containing IP options unless pass rules specifically allow them using the “Allow IP Options” checkbox in the Advanced section when editing a firewall rule (IP Options).
Since this is a special case, the firewall always logs when it drops these packets. However, the rule ID shown in this case is the rule the packet would have otherwise matched.
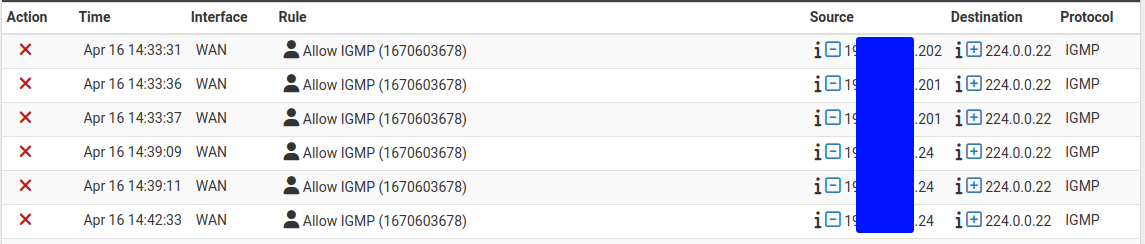
Log entries for packets blocked due to the presence of IP options¶
To resolve this, ensure any rules which should pass packets containing IP Options (e.g. IGMP) are configured to allow IP options.
See also
Asymmetric Routing¶
Blocked packets are also common for legitimate-looking traffic where routed networks and/or Multi-WAN are involved when Asymmetric Routing or other related causes are present in the network.
Clustering and Load Balancing¶
In a clustered environment, traffic arriving via the primary and leaving an internal interface can appear to be blocked on the secondary if the destination is a broadcast or multicast address like those used for Microsoft Network Load Balancing. The traffic appears to be blocked on the internal interface of the secondary from a public IP address source. Capturing the traffic on the secondary and inspecting the destination address in Wireshark will reveal the nature of the destination MAC address.